|
|
Order by Related
- New Release
- Rate
Results in Title For stealth
 | Stealth Inventory provides a small 100k agent that runs invisibly from the users login scripts. The agent transfers all data back to the central access database to allow easy analysis. .. |
|
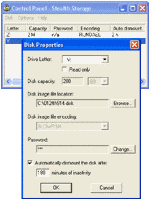 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. ..
|
|
 | EXE Stealth is a encrypter/protector for Windows to protect executable files PE against reverse engineering or cracking with a very strong protection.
Protections in EXE Stealth:
* Target file encrypted with user password (and automatic generation of a specific KeyGen)
* Target file encrypted with random key
* Anti-debugger techniques
* Anti-disassembler techniques
* Anti-generic dumper techniques
* Anti-VxD dumper techniques
* Anti-FrogsICE techniques
* Anti-Monitors techniques
* Anti-API spy techniques
* Random code insertion between each real instruction
* PE sections encryption
* Anti-patch techniques
* Virus detection
* Protection with multiple threads
* Polymorphic decryptors
* Threads decryptors
* Anti-hardware breakpoint decryptors
* Insertion of polymorphic anti-debugger code between each real instruction
* Insertion of polymorphic anti-disassembler code between each real instruction
* Ra .. |
|
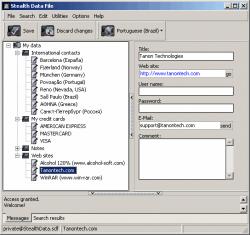 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy. ..
|
|
 | IMPORTANT ANNOUNCEMENT for wives, husbands, parents, girlfriends, boyfriends, employers, teachers ANYONE with a computer!
* Have you ever suspected your spouse or partner of CHEATING online and wanted to know NOW?
* Have you ever wondered what your kids are REALLY doing and seeing on the computer for hours on end?
* Have you ever wondered if your students are ONLY using school computers for educational purposes?
* Have you ever wanted to find out how much time your employees are REALLY wasting online?
Now, With The Help Of Stealth KeySpy 2.0, You Can:
* Find out where your spouse or partner have been online and what they've been doing!
* Protect your kids from Internet predators and offensive sites!
* Ensure your school or library computers are only being used for their intended purpose!
* Catch web-surfing employees red-handed!
You'll also be getting:
* A POWERFUL encryption utility for all YOUR emails and personal documents!
* A SECURE, real-time data back-up system!
* PLUS, an AUTOMATIC utility that records emails, chat sessions, instant messages, personal documents, files accessed, passwords, and web site visits!
ACCEPT NO IMITATIONS!
Stealth KeySpy 2.0 fully supports AOL, Yahoo, and Microsoft Messenger chat rooms, instant messaging programs, and emails. It even supports ICQ!
Available in several different languages, and comes with FREE lifetime upgrades, a 100% satisfaction GUARANTEE, plus an incredible AFFILIATE program that pays you 35%!
Stealth KeySpy 2.0 will outperform any program of its kind, offers more features and is less than half the cost of the competition!
--------------------------------------------------------------------------------
(C) Copyright ProfessionalGlobalMarketing.com 2001-2002.
All rights reserved. Reproduction in whole or in part without the written permission of the copyright owner is prohibited. .. |
|
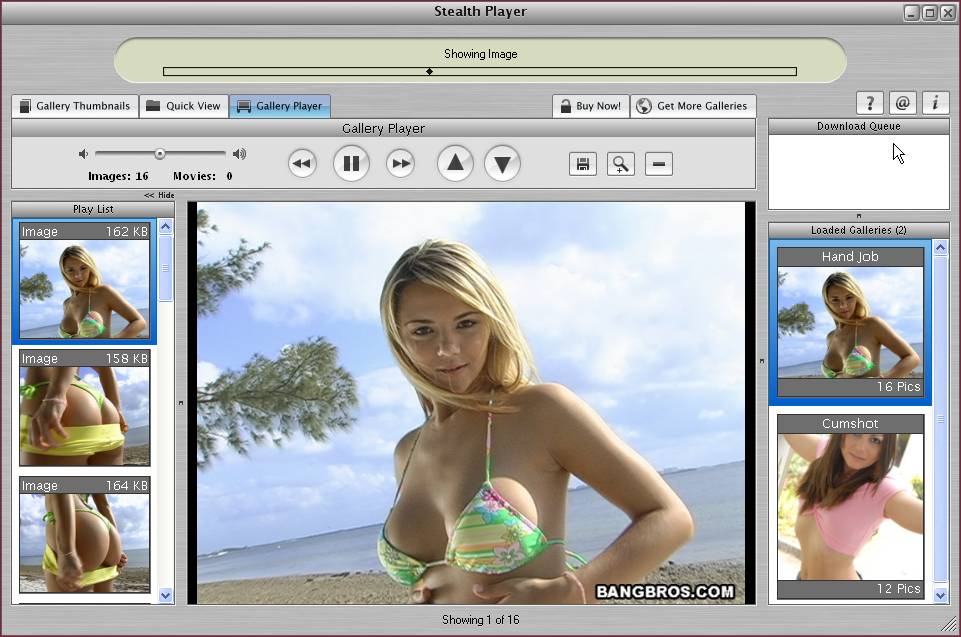 | Search our database of pre-screened and categorized galleries. We ..
|
|
 | Build Amazing banner advertising in a snap: text banners, add image(s), radio buttons...
Unlimites creativity is yours,make them rotate on your website and you get fresh updated content as you like The Banner Generator is an application through which you can create amazing banners for your site. The Banner generator is the smart and easiest way to create a banner.Banner Generator Provides following Functionalities 1) Drag and Drop Controls 2) Move and Resize controls using mouse 3) Easy assignment of properties to dragged controls 4) Variable sized banner creation (vertical and horizontal) (5) Adding, Editing, Deleting controls are easy to manage 6) Can save image as jpg, Gif, Bmp. .. |
|
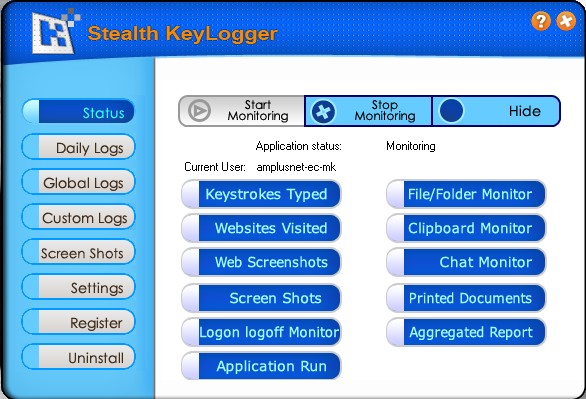 | Stealth KeyLogger is an invisible, easy to use surveillance application, designed to monitor and record all activities on a computer.
Perfectly suited for both office and home use Stealth KeyLogger offers detailed information on who uses your computer, their e-mails and chat conversations, the visited web sites, programs run as well as actual screenshots of their activity, websites visited and keystrokes history.You can schedule the exact period when you want that Stealth KeyLogger to monitor or, you can choose to exclude users from monitoring, and to specify when should the application record an user as being IDLE. On the other side there are new functionalities improved from the previous ones for a better surveillance in a better stealthy way.
This keylogger keeps up with the technology progress, so that the version of Internet Browsers and Instant Messaging applications does not influence the results of the application.
Reports are organized chronologically, always providing information on user, application and content (keystrokes, websites etc) and presented in a easy to read web format. For security reasons, reports may be printed or sent to a specified e-mail address. The improved email reporting gives you the liberty to choose which type of report you want to be send on e-mail, making the surveillance easier. You can also sent logs via Ftp, or save them to LAN. Stealth Keylogger can delete the old logs if the size specified is exceded.
Stealth KeyLogger has a hotkey and password activation protection and runs in stealth mode being undetectable in Task Manager (applications and processes). To save disk space, the program can clear logs periodically or after sending them to you. .. |
|
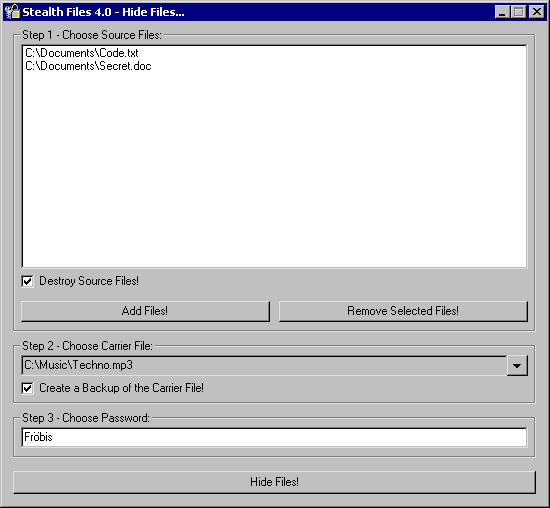 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files. .. |
|
 | The Stealth Recorder is a new kind of software that enables you to record any sounds secretly and transfer them automatically through email or ftp in perfect stealth mode. You can also record and send your voice message by e-mail with its powerful Voice Mail features. It records automatically whenever there are sounds and pauses as soon as there are no sounds. It supports realtime MP3 recording also.
Since it can transfer what is recorded to an email address or FTP site (in the stealth background state) automatically, you can easily send or receive the contents of a conference or a transcript of lectures promptly. You can make 'Voice Diary' yourself or listen to what is recorded long distance at the actual spot where you are now. So you can make the best use of this program in many ways. It is particularly possible to record a high quality sound automatically for long hours on the smallest hard disk space because of the supporting of MP3 realtime recording. If you have two computer units, one in your office and the other at home, you can listen to all kinds of voices or sounds in your own office or at home privately. .. |
|
Results in Keywords For stealth
 | With awesome "Metal Gear Solid" and "Splinter Cell" like game play, "Stealth Hunter" is a super-duper 20 mission action package of dangerous fun!.. |
|
 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc...
|
|
 | Backup and recover your system. With System Safe Stealth, you can automate your system backup and scan for potential problems. Rescue lost files automatically. Protect Against Cyber Terrorism. Your system is actively monitored and repairs are made as a preventative measure... |
|
 | div class=txt Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. It is totaly invisible when installed. Nobody will even notice there are encrypted files on a computer. Program runs on Windows 2000/XP systems only. /div..
|
|
 | Search our database of pre-screened and categorized galleries. We.. |
|
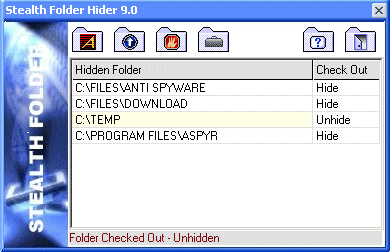 | Hide any folder on your PC. With Stealth Folder, folders and files can't be deleted, viewed, modified, or run. Stealth Folder Operates in Stealth mode, special hotkey is required to pull it up. Stealth Folder is not visible in Start, Toolbar, Taskbar, Add/Remove Programs or CTL ALT DEL.. Stealth Folder is Password Protected and you may hide as many folders as you wish. Stealth Folder comes with a Folder Hider and Clear Tracks utility...
|
|
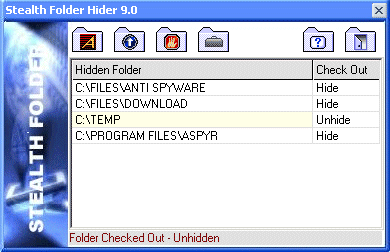 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder... |
|
Results in Description For stealth
 | Hide any folder on your PC. With Stealth Folder, folders and files can't be deleted, viewed, modified, or run. Stealth Folder Operates in Stealth mode, special hotkey is required to pull it up. Stealth Folder is not visible in Start, Toolbar, Taskbar, Add/Remove Programs or CTL ALT DEL.. Stealth Folder is Password Protected and you may hide as many folders as you wish. Stealth Folder comes with a Folder Hider and Clear Tracks utility... |
|
 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy...
|
|
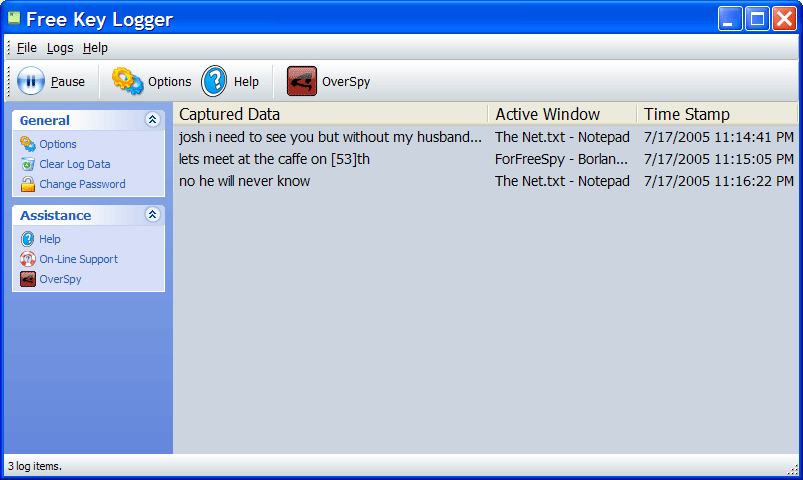 | Free Key Logger records everything that has been typed on a computer`s keyboard. It works in two modes: normal and stealth. In stealth mode it is virtually undetectable!.. |
|
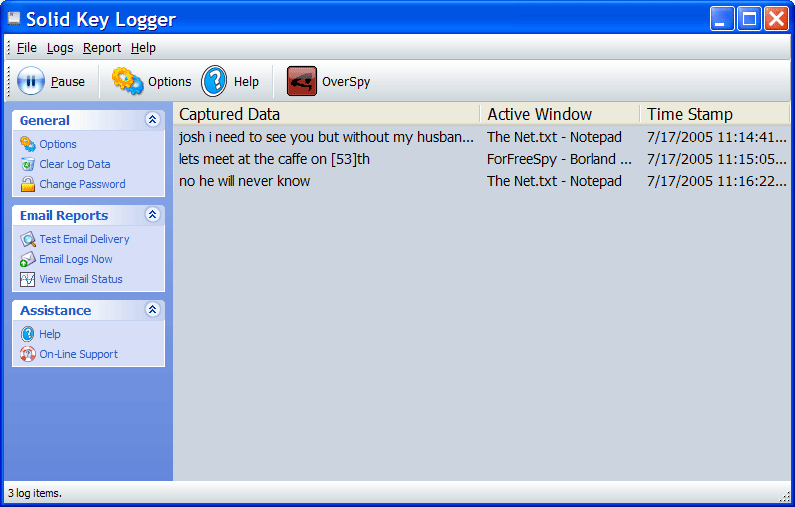 | Solid Key Logger records everything that has been typed on a computer`s keyboard. It works in two modes: normal and stealth. In stealth mode it is virtually undetectable!..
|
|
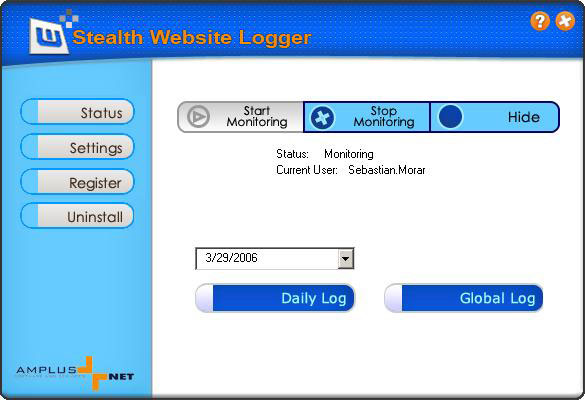 | Stealth Website Logger is an invisible, easy to use surveillance application that monitors and records all websites visited by a user or computer.
All accessed websites are recorded in a detailed report that can be viewed in web format or sent to a specified email address. Stealth Website Logger is suited for both office and home use, monitoring one computer or an entire network.
Fore enhanced security, Stealth Website Logger interface is password protected and requires a hotkey combination for accessing it. When running, Stealth Website Logger is not visible in Program Files and Task Manager... |
|
 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder...
|
|
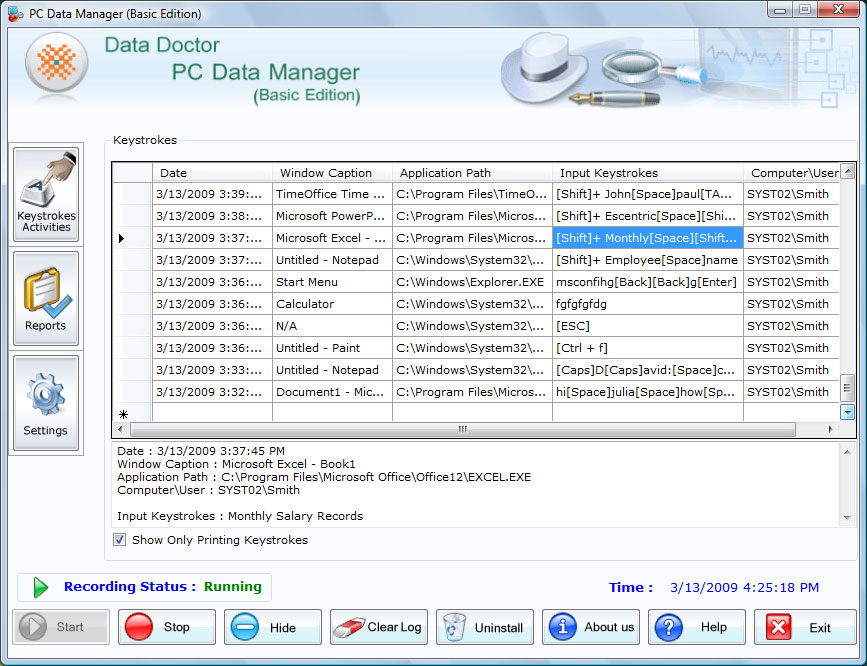 | Hidden keyboard logging software is cost-effective, reliable and safe tool that records every email sent from Yahoo, MSN, Hotmail, Gmail and many more internet browsing activities. Stealth recorder utility provides option to run in the stealth mode... |
|
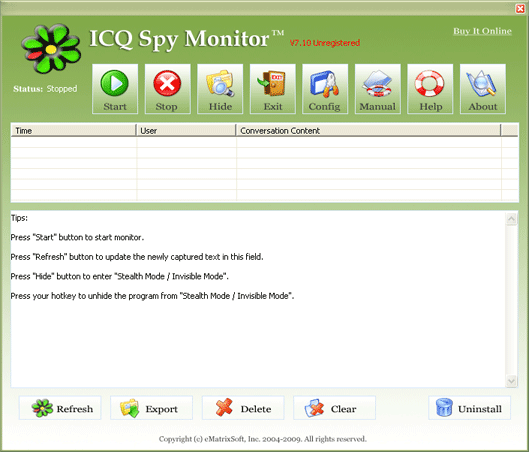 | Spy all version ICQ IM chatting records. Spy employees, children and spouse chatting on ICQ in stealth mode.Send reports to a set email address. Use hotkey to activate it from stealth mode and protect programaccess by password... |
|
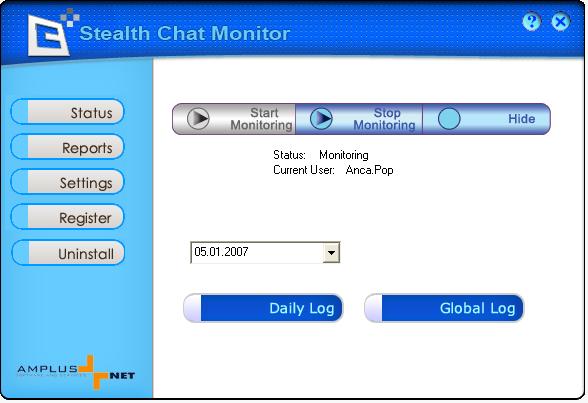 | Stealth Chat Monitor is an invisible, easy to use surveillance application, designed to monitor and record all chat conversations that took place on a computer.
Stealth Chat Monitor captures both sides of chat conversation from popular instant messaging services, like Yahoo Messenger, MSN, ICQ, IRC, Skype or Google Talk. The recorded information is saved chronologically in a detailed report that can be viewed in web format or sent to a specified email address.
This user-friendly application is not visible in Program Files and in Task Manager. For enhanced security, Stealth Chat Monitor's interface is password protected and requires a hotkey combination for accessing it... |
|
 | Stealth KeyLogger is an invisible, easy to use surveillance application, designed to monitor and record all activities on a computer.
Perfectly suited for both office and home use Stealth KeyLogger offers detailed information on who uses your computer, their e-mails and chat conversations, the visited web sites, programs run as well as actual screenshots of their activity, websites visited and keystrokes history.You can schedule the exact period when you want that Stealth KeyLogger to monitor or, you can choose to exclude users from monitoring, and to specify when should the application record an user as being IDLE. On the other side there are new functionalities improved from the previous ones for a better surveillance in a better stealthy way.
This keylogger keeps up with the technology progress, so that the version of Internet Browsers and Instant Messaging applications does not influence the results of the application.
Reports are organized chronologically, always providing information on user, application and content (keystrokes, websites etc) and presented in a easy to read web format. For security reasons, reports may be printed or sent to a specified e-mail address. The improved email reporting gives you the liberty to choose which type of report you want to be send on e-mail, making the surveillance easier. You can also sent logs via Ftp, or save them to LAN. Stealth Keylogger can delete the old logs if the size specified is exceded.
Stealth KeyLogger has a hotkey and password activation protection and runs in stealth mode being undetectable in Task Manager (applications and processes). To save disk space, the program can clear logs periodically or after sending them to you... |
|
Results in Tags For stealth
 | Backup and recover your system. With System Safe Stealth, you can automate your system backup and scan for potential problems. Rescue lost files automatically. Protect Against Cyber Terrorism. Your system is actively monitored and repairs are made as a preventative measure... |
|
 | div class=txt Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. It is totaly invisible when installed. Nobody will even notice there are encrypted files on a computer. Program runs on Windows 2000/XP systems only. /div..
|
|
 | Search our database of pre-screened and categorized galleries. We.. |
|
 | Stealth Chat Monitor is an invisible, easy to use surveillance application, designed to monitor and record all chat conversations that took place on a computer.
Stealth Chat Monitor captures both sides of chat conversation from popular instant messaging services, like Yahoo Messenger, MSN, ICQ, IRC, Skype or Google Talk. The recorded information is saved chronologically in a detailed report that can be viewed in web format or sent to a specified email address.
This user-friendly application is not visible in Program Files and in Task Manager. For enhanced security, Stealth Chat Monitor's interface is password protected and requires a hotkey combination for accessing it...
|
|
 | Stealth Cam the only way to take stolen shots.. |
|
 | Instant Stealth: Instantly make your workstation invisible to your network. Privacy: Eliminate snooping and monitoring of your workstation and files through your network. Security: Even if a hacker breaks into your network they will not be able to get into your workstation or your files. Neither will Net Admin or any other would be spy. You control ..
|
|
 | Stealth Anonymizer is a proxy server agent that lets you travel the Internet with maximum possible privacy. It contains a large autoupdated database of anonymous proxy servers and allows you to easily logon to them and test their anonymity. This network of publicly accessible servers shield your current connection when you visit websites, download files, or use web-based e-mail accounts. You can also block cookies with a single click of your mouse and very much more! .. |
|
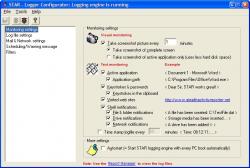 | This is a monitoring tool for both networked and personal PCs. It lets companies and individuals track use and abuse easily and invisibly using password-protected encrypted log files.
You can deploy this tool using e-mail. Simply send an e-mail to the person using the computer you want to monitor. STAR will then be installed silently on this computer and the person will never notice that this programm is running... |
|
 | Stealth wars, you can't be seen, avoid cameras, guards, and security lasers... |
|
 | Advanced SER enables you to collect copies of all the outgoing emails from the particular PC. This program monitors outgoing traffic of the target PC's email client and intercepts all the messages sent from it. Intercepted emails are forwarded to a pre-specified email address. Advanced Stealth Email Redirector (Advanced SER) does not intercept emails sent from web-based email services like www.yahoo.com, www.hotmail.com etc... |
|
Related search : tealth storage,stealth storage softwarestealth playeryouchat monitorstealth chat,stealth chat monitormonitor stealth chatchat monitor stealth,software free downloadinc software freestealth anonymizer,download stealth anonymizerfree download stealthsoOrder by Related
- New Release
- Rate
stealth.exe -
stealth labs -
stealth browser -
stealth ip -
stealth pe -
|
|




















