|
|
Order by Related
- New Release
- Rate
Results in Title For stealth files
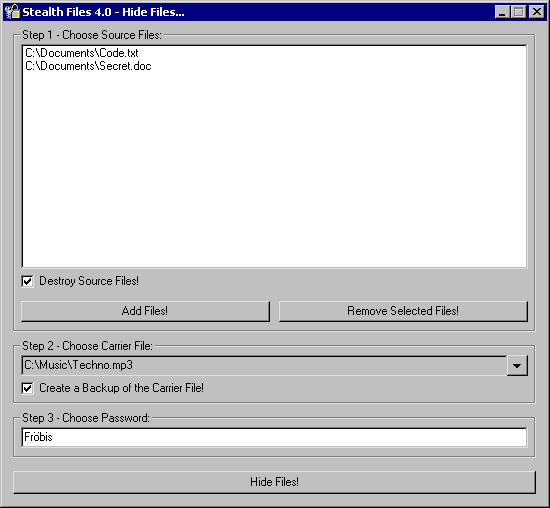 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files. .. |
|
 | Sends emails secretly without detection, bypasses corporate networks & tracking ..
|
|
 | With awesome "Metal Gear Solid" and "Splinter Cell" like game play, "Stealth Hunter" is a super-duper 20 mission action package of dangerous fun! .. |
|
 | Stealth Inventory provides a small 100k agent that runs invisibly from the users login scripts. The agent transfers all data back to the central access database to allow easy analysis. ..
|
|
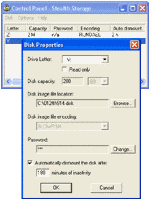 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. .. |
|
 | EXE Stealth is a encrypter/protector for Windows to protect executable files PE against reverse engineering or cracking with a very strong protection.
Protections in EXE Stealth:
* Target file encrypted with user password (and automatic generation of a specific KeyGen)
* Target file encrypted with random key
* Anti-debugger techniques
* Anti-disassembler techniques
* Anti-generic dumper techniques
* Anti-VxD dumper techniques
* Anti-FrogsICE techniques
* Anti-Monitors techniques
* Anti-API spy techniques
* Random code insertion between each real instruction
* PE sections encryption
* Anti-patch techniques
* Virus detection
* Protection with multiple threads
* Polymorphic decryptors
* Threads decryptors
* Anti-hardware breakpoint decryptors
* Insertion of polymorphic anti-debugger code between each real instruction
* Insertion of polymorphic anti-disassembler code between each real instruction
* Ra ..
|
|
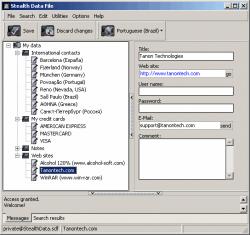 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy. .. |
|
 | IMPORTANT ANNOUNCEMENT for wives, husbands, parents, girlfriends, boyfriends, employers, teachers ANYONE with a computer!
* Have you ever suspected your spouse or partner of CHEATING online and wanted to know NOW?
* Have you ever wondered what your kids are REALLY doing and seeing on the computer for hours on end?
* Have you ever wondered if your students are ONLY using school computers for educational purposes?
* Have you ever wanted to find out how much time your employees are REALLY wasting online?
Now, With The Help Of Stealth KeySpy 2.0, You Can:
* Find out where your spouse or partner have been online and what they've been doing!
* Protect your kids from Internet predators and offensive sites!
* Ensure your school or library computers are only being used for their intended purpose!
* Catch web-surfing employees red-handed!
You'll also be getting:
* A POWERFUL encryption utility for all YOUR emails and personal documents!
* A SECURE, real-time data back-up system!
* PLUS, an AUTOMATIC utility that records emails, chat sessions, instant messages, personal documents, files accessed, passwords, and web site visits!
ACCEPT NO IMITATIONS!
Stealth KeySpy 2.0 fully supports AOL, Yahoo, and Microsoft Messenger chat rooms, instant messaging programs, and emails. It even supports ICQ!
Available in several different languages, and comes with FREE lifetime upgrades, a 100% satisfaction GUARANTEE, plus an incredible AFFILIATE program that pays you 35%!
Stealth KeySpy 2.0 will outperform any program of its kind, offers more features and is less than half the cost of the competition!
--------------------------------------------------------------------------------
(C) Copyright ProfessionalGlobalMarketing.com 2001-2002.
All rights reserved. Reproduction in whole or in part without the written permission of the copyright owner is prohibited. .. |
|
 | Build Amazing banner advertising in a snap: text banners, add image(s), radio buttons...
Unlimites creativity is yours,make them rotate on your website and you get fresh updated content as you like The Banner Generator is an application through which you can create amazing banners for your site. The Banner generator is the smart and easiest way to create a banner.Banner Generator Provides following Functionalities 1) Drag and Drop Controls 2) Move and Resize controls using mouse 3) Easy assignment of properties to dragged controls 4) Variable sized banner creation (vertical and horizontal) (5) Adding, Editing, Deleting controls are easy to manage 6) Can save image as jpg, Gif, Bmp. .. |
|
 | Search our database of pre-screened and categorized galleries. We .. |
|
Results in Keywords For stealth files
 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files... |
|
 | Eliminate all evidence from your hard drive and protect your privacy. Clean out all your secrets/files of your browser's cache, cookies, sites visited, urls visited, images viewed, media files played and forms files...
|
|
 | A quick and easy way to protect sensitive information on your computer from children, employers, roommates and anyone else who uses your computer, including hackers! A hacker can't steal what they don't know exists to begin with... |
|
 | Hide Those Folders is the best way for you to hide folders and hide files and keep sensitive and important data hidden from view. Hide files and hide folders from Children, Employers, Anyone else at all, even hackers! ..
|
|
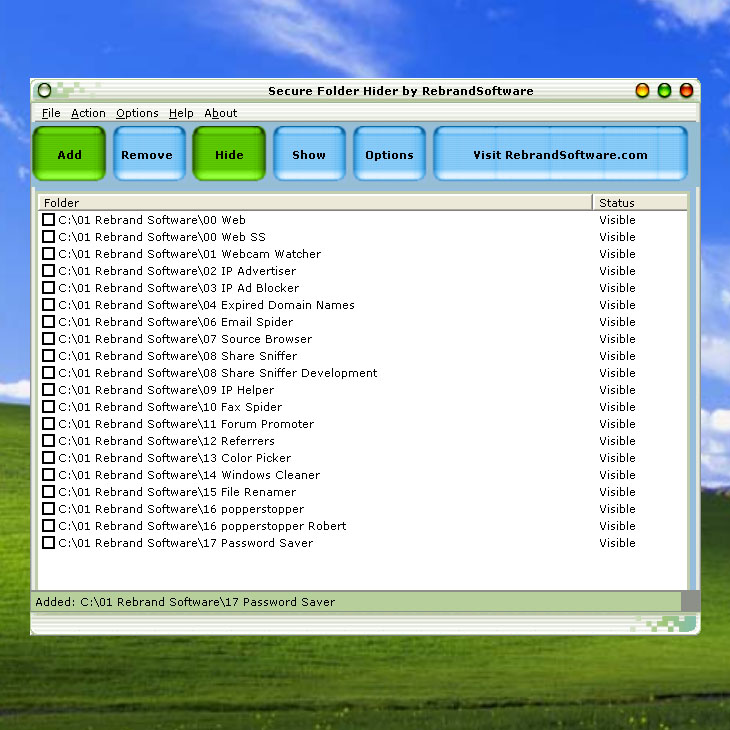 | A quick and easy way to protect sensitive information on your computer from children, employers, and anyone else who uses your computer, including hackers!.. |
|
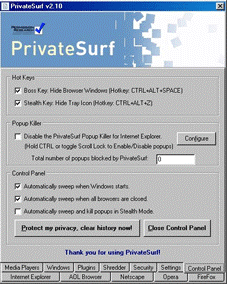 | Keep Your Internet Surfing Activity Private with PrivateSurf!
Clear Temporary Internet Files
Browsers store an extensive amount of information from web pages you have visited that can stay on your computer for months! PrivateSurf allows you to securely clear this information from your machine.
Clear Browser History Files and Browser URL Drop Down List
Each URL that you visit is stored in the Browser History Files. This information can show an exact map of where and when you surfed all the websites you have ever visited. Plus each time you type a website address it is stored. PrivateSurf allows you to securely clear this information from your machine.
Clear Website Cookies
Most web sites save information in the form of "Cookies" on your machine when you visit them. In order to avoid being tracked by these cookies, PrivateSurf will delete the cookies on a regular basis, helping to protect your privacy.
Clear Cache and Index.dat Files
There are three index.dat files used by Internet Explorer that cannot be removed while Internet Explorer is running. They store index information which can show what sites you have visited. PrivateSurf allows you to delete these files when Windows boots but before Windows locks them.
Blocks Popups
Many websites have popup advertisements. PrivateSurf makes sure these popup advertisements do not appear.
Stealth Key: Hide PrivateSurf Tray Icon
The Stealth Key allows you to hide the PrivateSurf Tray Icon so that no one will know you are running PrivateSurf. Combined with Stealth Mode, PrivateSurf becomes invisible to the casual observer.
Protects Internet Explorer Homepage from changes by websites
Some websites might trick you into changing your home page. PrivateSurf will make sure that your homepage is set back to the original homepage you had set at the beginning of the current session.
Best of all, PrivateSurf is Free for PermissionResearch Members!..
|
|
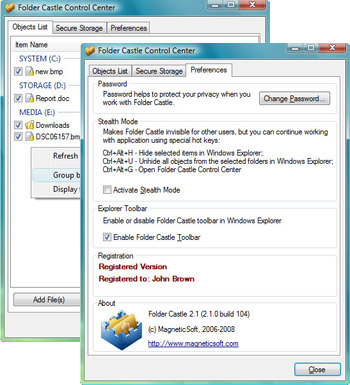 | Folder Castle is a powerful and easy-to-use software for protection of private and confidential information on your computer. In a few seconds it will help you to hide documents, images, files, folders and drives on your computer. Nobody will even know that you store private information because Folder Castle will hide files from other users. Hidden files become completely inaccessible for others: they cannot be read, copied, moved, deleted or just seen. Protected files are not visible in Windows Explorer or any other program. Files are password protected, so nobody can access them without knowing your password. Also the application protects files from accessing by viruses, trojans and spyware. To raise the security Folder Castle has Stealth mode. It prevents the very attempt of hackers' access to your confident data. In Stealth mode nobody will even know that the application is installed, and protected data is stored on the computer.
Folder Castle benefits:
- Possibility to hide documents, images, files and drives from any user including local administrator
- Denied access to hidden files by any application, including viruses, trojans and other spyware
- Compatible with Windows Vista
- Friendly user interface, fast commands execution in Windows Explorer via either toolbar or context menus or hot keys
- Password protection of commands execution
- Possibility to recover lost password (for registered users)
- Unlimited number of hidden documents, images, files and drives (for registered users)
- Stealth mode for improved security.. |
|
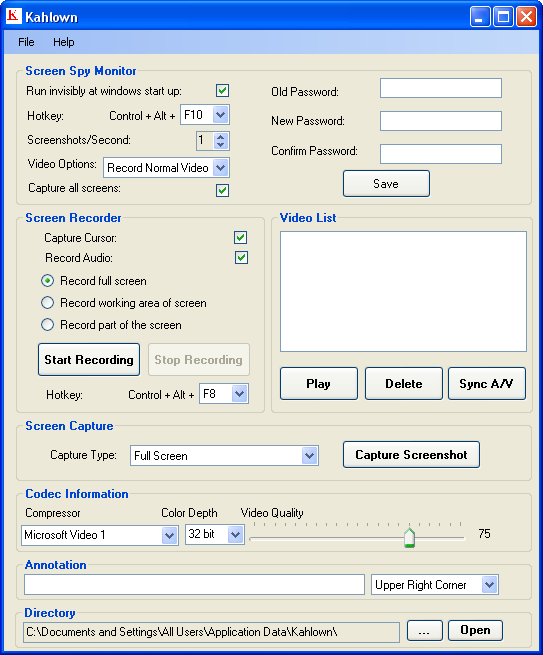 | Kahlown is screen capturing, screen recording and screen spying software. Kahlown provides an array of screen capturing and screen recording features. Stealth mode to record screen invisibly to monitor children. Sync audio video lag in video files... |
|
 | Stealth wars, you can't be seen, avoid cameras, guards, and security lasers... |
|
 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy... |
|
Results in Description For stealth files
 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files... |
|
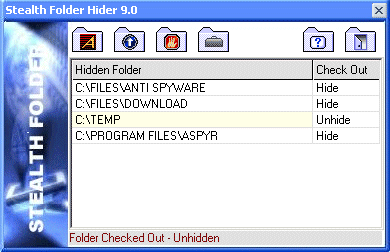 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder...
|
|
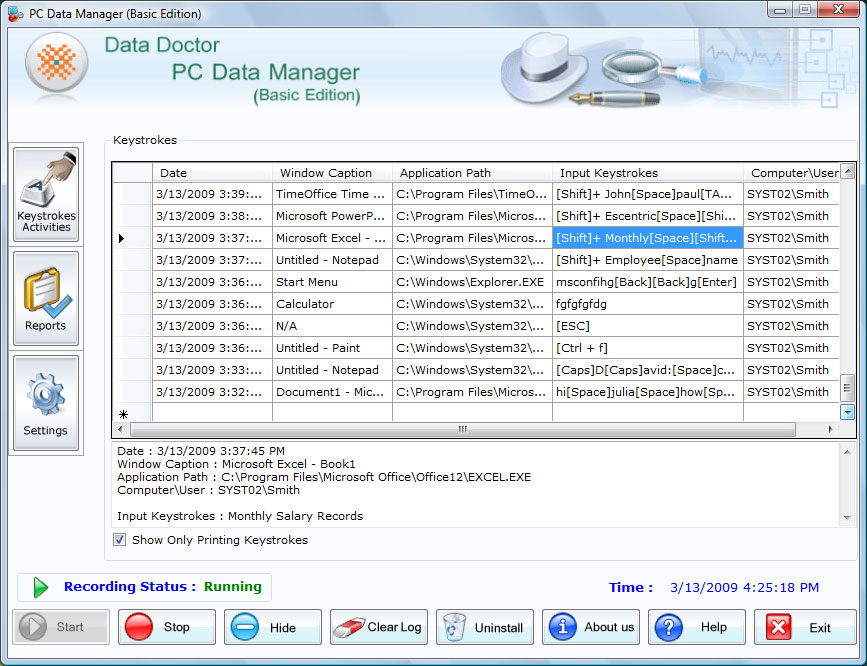 | Hidden keyboard logging software is cost-effective, reliable and safe tool that records every email sent from Yahoo, MSN, Hotmail, Gmail and many more internet browsing activities. Stealth recorder utility provides option to run in the stealth mode... |
|
 | Stealth Chat Monitor is an invisible, easy to use surveillance application, designed to monitor and record all chat conversations that took place on a computer.
Stealth Chat Monitor captures both sides of chat conversation from popular instant messaging services, like Yahoo Messenger, MSN, ICQ, IRC, Skype or Google Talk. The recorded information is saved chronologically in a detailed report that can be viewed in web format or sent to a specified email address.
This user-friendly application is not visible in Program Files and in Task Manager. For enhanced security, Stealth Chat Monitor's interface is password protected and requires a hotkey combination for accessing it...
|
|
 | Spy all version ICQ IM chatting records. Spy employees, children and spouse chatting on ICQ in stealth mode.Send reports to a set email address. Use hotkey to activate it from stealth mode and protect programaccess by password... |
|
 | Stealth KeyLogger is an invisible, easy to use surveillance application, designed to monitor and record all activities on a computer.
Perfectly suited for both office and home use Stealth KeyLogger offers detailed information on who uses your computer, their e-mails and chat conversations, the visited web sites, programs run as well as actual screenshots of their activity, websites visited and keystrokes history.You can schedule the exact period when you want that Stealth KeyLogger to monitor or, you can choose to exclude users from monitoring, and to specify when should the application record an user as being IDLE. On the other side there are new functionalities improved from the previous ones for a better surveillance in a better stealthy way.
This keylogger keeps up with the technology progress, so that the version of Internet Browsers and Instant Messaging applications does not influence the results of the application.
Reports are organized chronologically, always providing information on user, application and content (keystrokes, websites etc) and presented in a easy to read web format. For security reasons, reports may be printed or sent to a specified e-mail address. The improved email reporting gives you the liberty to choose which type of report you want to be send on e-mail, making the surveillance easier. You can also sent logs via Ftp, or save them to LAN. Stealth Keylogger can delete the old logs if the size specified is exceded.
Stealth KeyLogger has a hotkey and password activation protection and runs in stealth mode being undetectable in Task Manager (applications and processes). To save disk space, the program can clear logs periodically or after sending them to you...
|
|
 | P-Encryption Suite is a powerful encryption program for the windows operating system used to store your private documents into a single encrypted file. There are two different encrypted archives P-Encryption Suite can create, Stealth and Normal. Stealth archives are PES archives disguised as a different file, such as an image or audio file. You can also take your encrypted data with you anywhere you go by using CD/DVD encryption... |
|
 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc... |
|
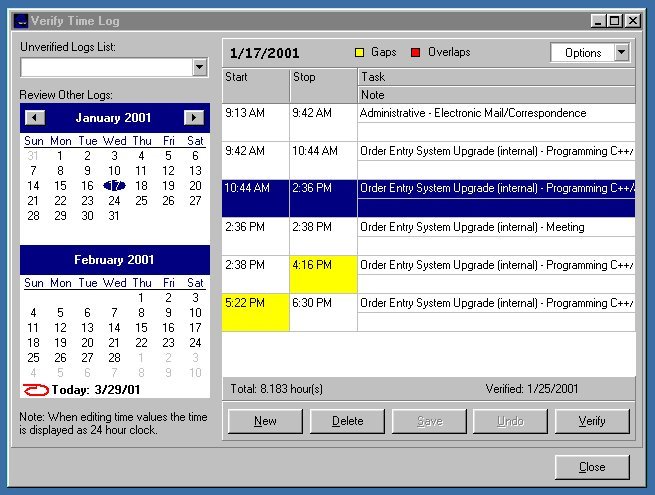 | Shadow Professional erases evidence of your web activity and cleans history embed on your computer. Press Start and surf without evidence. Full support for Internet Explorer, AOL, Firefox, Netscape and Opera. Over 240 plug-ins to remove evidence from popular programs like ACDSee, Media Player, MS Office, eMule and other p2p programs. Secret bookmarks to make your web links hidden, Secret Folders to hide and encrypt private files even in safe mode, Shredder to delete files beyond recovery. It uses top secure algorithms of Defense DoD 5220.22-M. Disk Wiper, Evidence Eraser, Boss Key, Stealth Mode, Plug-Ins, Scheduler, Profiles, Managers, password protection from unauthorized use, Panic Keys, Stealth Mode... |
|
 | Folder Castle is a powerful and easy-to-use software for protection of private and confidential information on your computer. In a few seconds it will help you to hide documents, images, files, folders and drives on your computer. Nobody will even know that you store private information because Folder Castle will hide files from other users. Hidden files become completely inaccessible for others: they cannot be read, copied, moved, deleted or just seen. Protected files are not visible in Windows Explorer or any other program. Files are password protected, so nobody can access them without knowing your password. Also the application protects files from accessing by viruses, trojans and spyware. To raise the security Folder Castle has Stealth mode. It prevents the very attempt of hackers' access to your confident data. In Stealth mode nobody will even know that the application is installed, and protected data is stored on the computer.
Folder Castle benefits:
- Possibility to hide documents, images, files and drives from any user including local administrator
- Denied access to hidden files by any application, including viruses, trojans and other spyware
- Compatible with Windows Vista
- Friendly user interface, fast commands execution in Windows Explorer via either toolbar or context menus or hot keys
- Password protection of commands execution
- Possibility to recover lost password (for registered users)
- Unlimited number of hidden documents, images, files and drives (for registered users)
- Stealth mode for improved security.. |
|
Results in Tags For stealth files
 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files... |
|
 | Stealth wars, you can't be seen, avoid cameras, guards, and security lasers...
|
|
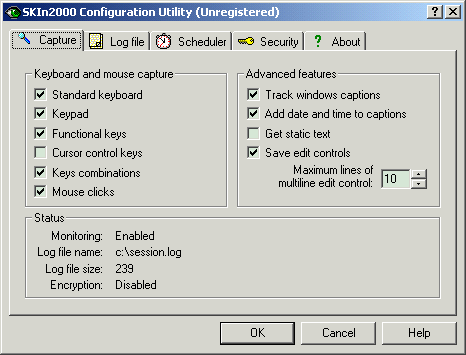 | Stealth Keyboard Interceptor for Windows NT/2000/ XP (SKIn2000) is a monitoring program which allows to intercept all keystrokes, mouse clicks, captions of active windows, static text and other... |
|
 | Eliminate all evidence from your hard drive and protect your privacy. Clean out all your secrets/files of your browser's cache, cookies, sites visited, urls visited, images viewed, media files played and forms files...
|
|
 | Folder Castle is a powerful and easy-to-use software for protection of private and confidential information on your computer. In a few seconds it will help you to hide documents, images, files, folders and drives on your computer. Nobody will even know that you store private information because Folder Castle will hide files from other users. Hidden files become completely inaccessible for others: they cannot be read, copied, moved, deleted or just seen. Protected files are not visible in Windows Explorer or any other program. Files are password protected, so nobody can access them without knowing your password. Also the application protects files from accessing by viruses, trojans and spyware. To raise the security Folder Castle has Stealth mode. It prevents the very attempt of hackers' access to your confident data. In Stealth mode nobody will even know that the application is installed, and protected data is stored on the computer.
Folder Castle benefits:
- Possibility to hide documents, images, files and drives from any user including local administrator
- Denied access to hidden files by any application, including viruses, trojans and other spyware
- Compatible with Windows Vista
- Friendly user interface, fast commands execution in Windows Explorer via either toolbar or context menus or hot keys
- Password protection of commands execution
- Possibility to recover lost password (for registered users)
- Unlimited number of hidden documents, images, files and drives (for registered users)
- Stealth mode for improved security.. |
|
 | Stealth KeyLogger is an invisible, easy to use surveillance application, designed to monitor and record all activities on a computer.
Perfectly suited for both office and home use Stealth KeyLogger offers detailed information on who uses your computer, their e-mails and chat conversations, the visited web sites, programs run as well as actual screenshots of their activity, websites visited and keystrokes history.You can schedule the exact period when you want that Stealth KeyLogger to monitor or, you can choose to exclude users from monitoring, and to specify when should the application record an user as being IDLE. On the other side there are new functionalities improved from the previous ones for a better surveillance in a better stealthy way.
This keylogger keeps up with the technology progress, so that the version of Internet Browsers and Instant Messaging applications does not influence the results of the application.
Reports are organized chronologically, always providing information on user, application and content (keystrokes, websites etc) and presented in a easy to read web format. For security reasons, reports may be printed or sent to a specified e-mail address. The improved email reporting gives you the liberty to choose which type of report you want to be send on e-mail, making the surveillance easier. You can also sent logs via Ftp, or save them to LAN. Stealth Keylogger can delete the old logs if the size specified is exceded.
Stealth KeyLogger has a hotkey and password activation protection and runs in stealth mode being undetectable in Task Manager (applications and processes). To save disk space, the program can clear logs periodically or after sending them to you...
|
|
 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc... |
|
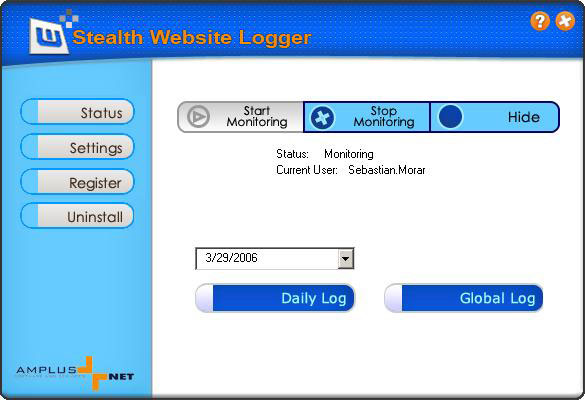 | Stealth Website Logger is an invisible, easy to use surveillance application that monitors and records all websites visited by a user or computer.
All accessed websites are recorded in a detailed report that can be viewed in web format or sent to a specified email address. Stealth Website Logger is suited for both office and home use, monitoring one computer or an entire network.
Fore enhanced security, Stealth Website Logger interface is password protected and requires a hotkey combination for accessing it. When running, Stealth Website Logger is not visible in Program Files and Task Manager... |
|
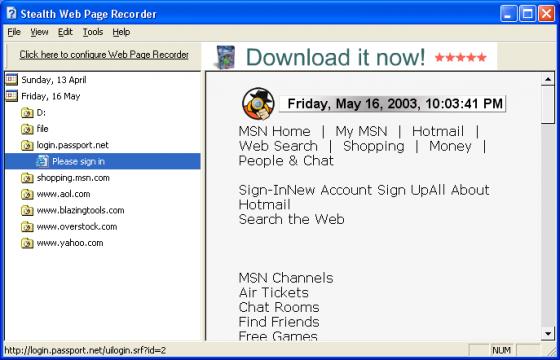 | The Stealth Recorder is a new kind of software that enables you to record any sounds secretly and transfer them automatically through email or ftp in perfect stealth mode. You can also record and send your voice message by e-mail with its powerful Voice Mail features. It records automatically whenever there are sounds and pauses as soon as there are no sounds. It supports realtime MP3 recording also.
Since it can transfer what is recorded to an email address or FTP site (in the stealth background state) automatically, you can easily send or receive the contents of a conference or a transcript of lectures promptly. You can make 'Voice Diary' yourself or listen to what is recorded long distance at the actual spot where you are now. So you can make the best use of this program in many ways. It is particularly possible to record a high quality sound automatically for long hours on the smallest hard disk space because of the supporting of MP3 realtime recording. If you have two computer units, one in your office and the other at home, you can listen to all kinds of voices or sounds in your own office or at home privately... |
|
 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder... |
|
Related search : tealth wars,1000 stealth warsinterceptor forkeyboard interceptorstealth keyboard,stealth keyboard interceptorprivacy protectorstealth privacy,stealth privacy protectorprotect your privacyprivacy protector stealthprotector stealth privacyfolder castleOrder by Related
- New Release
- Rate
stealth anonymizer -
stealth keylogger 4.9 -
stealth pc -
stealth.exe -
stealth labs -
|
|
























