|
|
Order by Related
- New Release
- Rate
Results in Title For stealth ip
 | While the operation of different facilities, which are connected to a computer via serial port, there may appear the necessity to start up utility program (for these facilities) not in the machine, to which the facilities connect directly, but in the remote machine, that is connected to the facility server via the network (TCP/IP).
The developers of the given facilities very often face with such a necessity. For instance, during the debugging in a remote machine or when different people with the help of different machines (which are nevertheless connected to one machine) maintain the same facilities.
AVSD.IP is designed especially for the solving of these problems. The use of our product gives you the possibility to give the remote access to serial port via TCP/IP. The product consists of three parts:
1. AVSD is a program emulator of serial ports (up to 255) for operational system W2K/XP.
2. AVSD.IP client is the service, which realizes the exchange between AVSD and TCP/IP.
3. AVSD.IP server is a service which realizes the exchange between a real driver of the serial port and TCP/IP.
AVSD.IP client and server handle two flows: outcoming and incoming.
The client takes the bytes that were transferred to all the virtual ports earlier and then transfers them to the server, which was started up on the other computer. Also the client receives flows from the server and gives the bytes (as those which came from the outside) to AVSD.
IP address of the receiving server, port number and the number of the real serial port on the receiver are specified on the client for each port.
The server receives the information from clients and then transfers it to the ports specified by them. As for the flows, which came from these ports, the server transfers them to the client as well. Besides the data flow, TCP/IP transfers the overhead information about the condition of different signals on serial port physical contacts. .. |
|
 | IP Ware was created to enable the individual investor tosucceed in the complex world of Real Estate Investing. Thisuser-friendly program allows you to determine your profitfrom a real estate investment, and provides the analysisnecessary to create perpetual cash flows from the purchaseof a property. ..
|
|
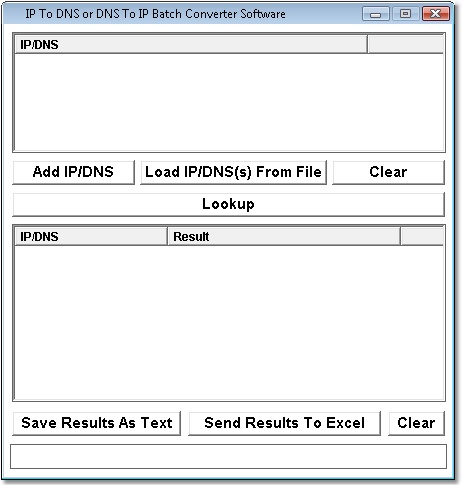 | Convert multiple IP addresses to DNS addresses and vice versa. .. |
|
 | Sends emails secretly without detection, bypasses corporate networks & tracking ..
|
|
 | With awesome "Metal Gear Solid" and "Splinter Cell" like game play, "Stealth Hunter" is a super-duper 20 mission action package of dangerous fun! .. |
|
 | Stealth Inventory provides a small 100k agent that runs invisibly from the users login scripts. The agent transfers all data back to the central access database to allow easy analysis. ..
|
|
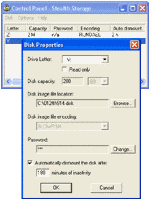 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. .. |
|
 | EXE Stealth is a encrypter/protector for Windows to protect executable files PE against reverse engineering or cracking with a very strong protection.
Protections in EXE Stealth:
* Target file encrypted with user password (and automatic generation of a specific KeyGen)
* Target file encrypted with random key
* Anti-debugger techniques
* Anti-disassembler techniques
* Anti-generic dumper techniques
* Anti-VxD dumper techniques
* Anti-FrogsICE techniques
* Anti-Monitors techniques
* Anti-API spy techniques
* Random code insertion between each real instruction
* PE sections encryption
* Anti-patch techniques
* Virus detection
* Protection with multiple threads
* Polymorphic decryptors
* Threads decryptors
* Anti-hardware breakpoint decryptors
* Insertion of polymorphic anti-debugger code between each real instruction
* Insertion of polymorphic anti-disassembler code between each real instruction
* Ra .. |
|
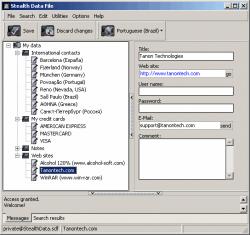 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy. .. |
|
 | IMPORTANT ANNOUNCEMENT for wives, husbands, parents, girlfriends, boyfriends, employers, teachers ANYONE with a computer!
* Have you ever suspected your spouse or partner of CHEATING online and wanted to know NOW?
* Have you ever wondered what your kids are REALLY doing and seeing on the computer for hours on end?
* Have you ever wondered if your students are ONLY using school computers for educational purposes?
* Have you ever wanted to find out how much time your employees are REALLY wasting online?
Now, With The Help Of Stealth KeySpy 2.0, You Can:
* Find out where your spouse or partner have been online and what they've been doing!
* Protect your kids from Internet predators and offensive sites!
* Ensure your school or library computers are only being used for their intended purpose!
* Catch web-surfing employees red-handed!
You'll also be getting:
* A POWERFUL encryption utility for all YOUR emails and personal documents!
* A SECURE, real-time data back-up system!
* PLUS, an AUTOMATIC utility that records emails, chat sessions, instant messages, personal documents, files accessed, passwords, and web site visits!
ACCEPT NO IMITATIONS!
Stealth KeySpy 2.0 fully supports AOL, Yahoo, and Microsoft Messenger chat rooms, instant messaging programs, and emails. It even supports ICQ!
Available in several different languages, and comes with FREE lifetime upgrades, a 100% satisfaction GUARANTEE, plus an incredible AFFILIATE program that pays you 35%!
Stealth KeySpy 2.0 will outperform any program of its kind, offers more features and is less than half the cost of the competition!
--------------------------------------------------------------------------------
(C) Copyright ProfessionalGlobalMarketing.com 2001-2002.
All rights reserved. Reproduction in whole or in part without the written permission of the copyright owner is prohibited. .. |
|
Results in Keywords For stealth ip
 | Stealth wars, you can't be seen, avoid cameras, guards, and security lasers... |
|
 | Data Stealth v1.0 is a complete and effective encryption package for both the home and business user. Data Stealth allows users to hide private information within audio and video files, without worrying if their data will remain secure. Data Stealth is packed with 3 extremely advanced encryption algorithms to ensure that any data protected with Data Stealth, remains protected. Users can now securely store and transfer extremely large amounts of data without compromising privacy...
|
|
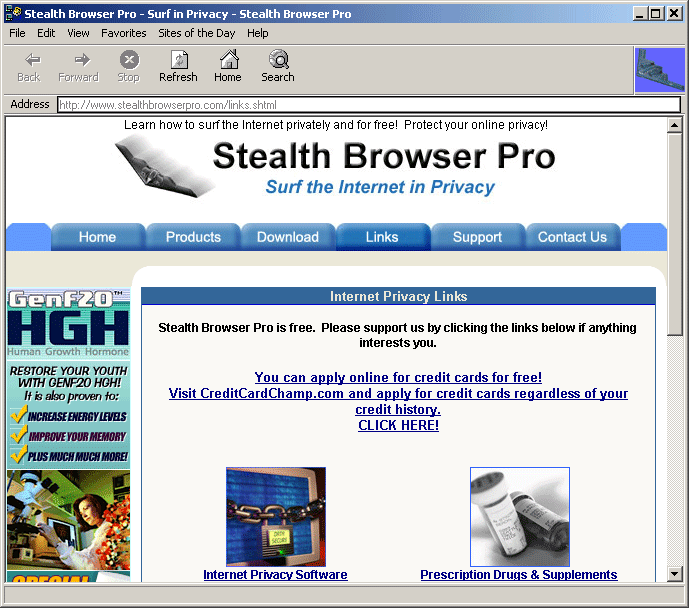 | Now you can privately surf to ANY type of website you want with Stealth Browser Pro, a FREE password protected privacy browser. Your privacy is protected because it has a login that hides as a dial-up connection so only you know it's there and your history file, cache, index.dat and permanent cookies are not written to. Nobody can go behind you on your computer and see where you've been and no web sites will show up in your history. Even the URLs you type are light shades of grey instead of black to help protect you from prying eyes. We even provide you with a list of favorites (bookmarks) to help you easily find the websites you are looking for. NEVER EXPIRES!!.. |
|
 | With awesome "Metal Gear Solid" and "Splinter Cell" like game play, "Stealth Hunter" is a super-duper 20 mission action package of dangerous fun!..
|
|
 | Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc... |
|
 | Backup and recover your system. With System Safe Stealth, you can automate your system backup and scan for potential problems. Rescue lost files automatically. Protect Against Cyber Terrorism. Your system is actively monitored and repairs are made as a preventative measure...
|
|
 | div class=txt Stealth Storage is a small and powerful file encryption tool. It encrypts files on-the-fly using well-known strong ciphers like BLOWFISH, RIJNDAEL etc. It is totaly invisible when installed. Nobody will even notice there are encrypted files on a computer. Program runs on Windows 2000/XP systems only. /div.. |
|
 | Search our database of pre-screened and categorized galleries. We.. |
|
 | Hide any folder on your PC. With Stealth Folder, folders and files can't be deleted, viewed, modified, or run. Stealth Folder Operates in Stealth mode, special hotkey is required to pull it up. Stealth Folder is not visible in Start, Toolbar, Taskbar, Add/Remove Programs or CTL ALT DEL.. Stealth Folder is Password Protected and you may hide as many folders as you wish. Stealth Folder comes with a Folder Hider and Clear Tracks utility... |
|
 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder... |
|
Results in Description For stealth ip
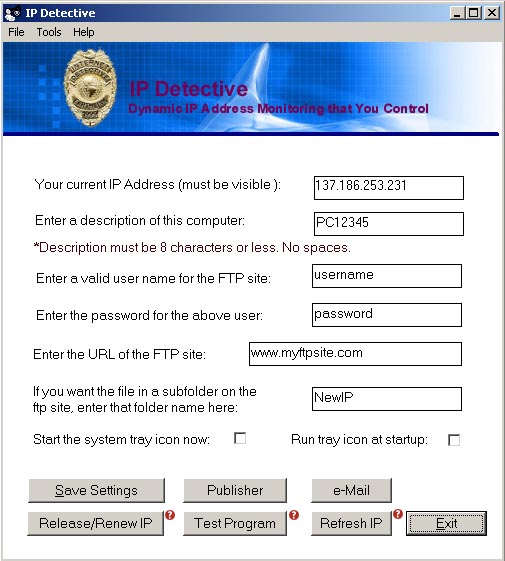 | IP Detective Suite is an IP monitoring program that reports your changing IP address
to your ftp site, e-mails it to you and displays it on your desktop. This makes a perfect
tool for remote connection with programs such as pcAnywhere. IP Detective Suite inlcudes
IP Detective Original IP Publisher, IP e-mail alert and IP Desktop Viewer with copy to
clipboard function. Publisher stores changind ip address to any computer you wish and
publishes them in a list using IP Publisher. Monitor an unlimited number of ip addresses.
Access a published list from any computer... |
|
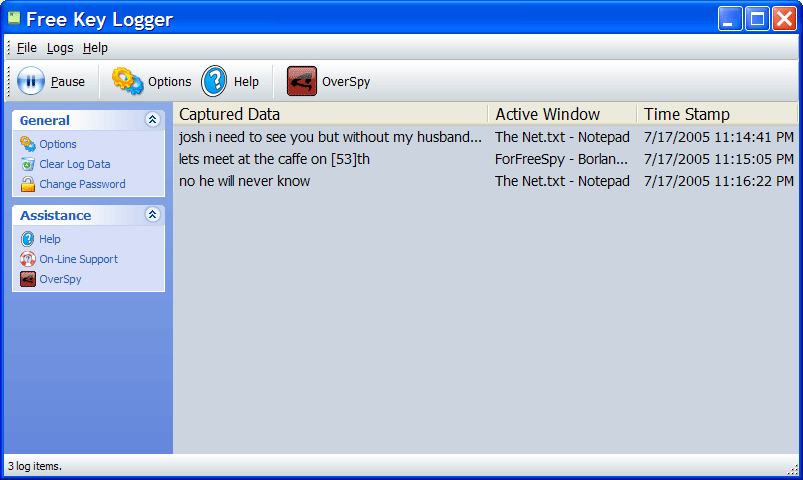 | Free Key Logger records everything that has been typed on a computer`s keyboard. It works in two modes: normal and stealth. In stealth mode it is virtually undetectable!..
|
|
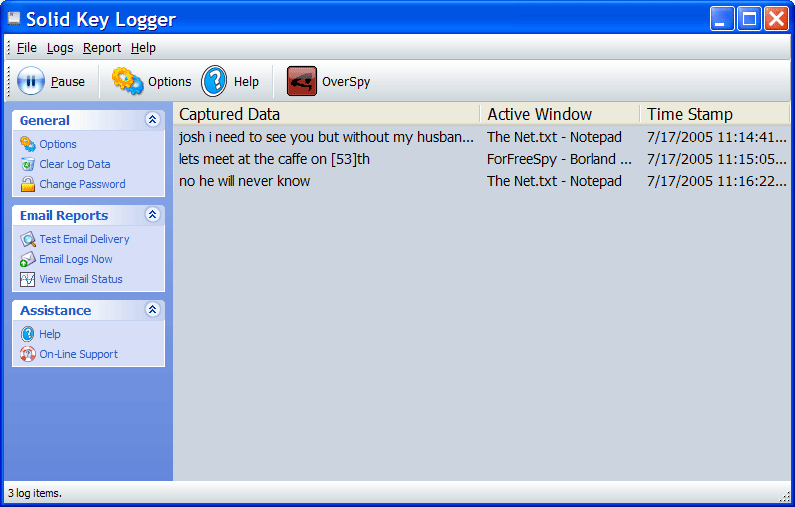 | Solid Key Logger records everything that has been typed on a computer`s keyboard. It works in two modes: normal and stealth. In stealth mode it is virtually undetectable!.. |
|
 | IP Detective Suite is an ideal program for anyone using a dynamic IP address. IP Detective Suite will report any changes in your dynamic IP to your ftp site, it will e-mail your new IP to you (will e-mail it to up to two e-mail addresses) and will also displays your IP on your desktop using IP Desktop Viewer with copy to clipboard and the new always on top feature. The newest version will also allow you to release and renew your dynamic IP when you deem it necessary and you will also be able to test the application with our new test feature...
|
|
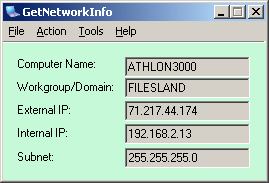 | If you are running an ftp server on your local computer or giving access to your colleagues via IP address it is important to detect changes of your external IP. This software monitors changes of your external IP and displays major network parameters of your cumputer such as: computer name, workgroup or domain, internal IP and subnet, external IP. If the external IP of your P has changed, GetNetowrkInfo will display a popup notification message or play sound... |
|
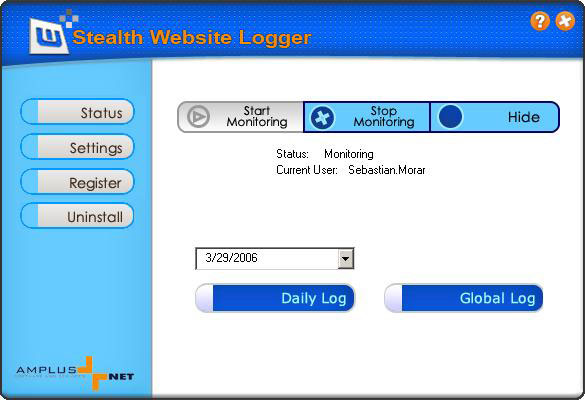 | Stealth Website Logger is an invisible, easy to use surveillance application that monitors and records all websites visited by a user or computer.
All accessed websites are recorded in a detailed report that can be viewed in web format or sent to a specified email address. Stealth Website Logger is suited for both office and home use, monitoring one computer or an entire network.
Fore enhanced security, Stealth Website Logger interface is password protected and requires a hotkey combination for accessing it. When running, Stealth Website Logger is not visible in Program Files and Task Manager...
|
|
 | Stealth folder is password protected. Stealth Folder also comes with Clear Tracks and File shredder... |
|
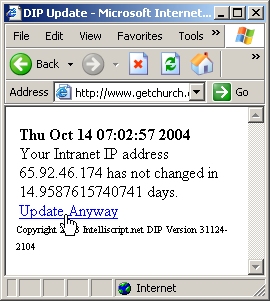 | This free Dynamic IP Direct script automates the process of updating an ever-changing IP address. Dial-up; even Home DSL and Cable connections can change your IP address without warning, unless you pay big-bucks for a static IP. This script reports your IP to any subdomain site like CJB. net, and saves your real IP to a text file on the server. Have multiple domains? No problem. This script will sequentially report to the domains when your IP address changes, so no matter how your web visitors find your site, you can rest assured they'll get there without any problems... |
|
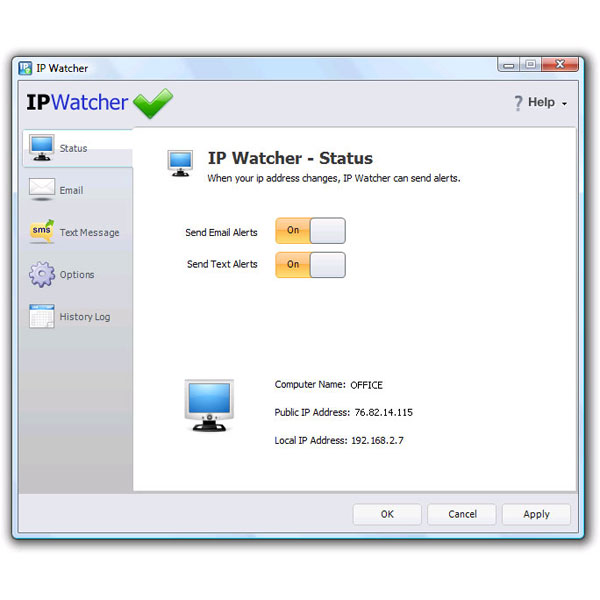 | IP Watcher monitors your public and local IP address. If your IP address changes it will send an email or SMS Text Message alert containing the new IP address. This alert also includes the computer name, local ip address and time the change occurred... |
|
 | Dynamic IP Update Service is simply a way of attaching a static hostname to a dynamic IP address.
On the Internet, there are a limited number of IP addresses. When you connect to your ISP, you are assigned a temporary IP address that other computers use to find you while you are connected. Once you disconnect, that IP address is given to someone else, and so on. If you are trying to operate a gaming server, personal web server, or any other service that requires other computers to be able to find you, they need to know what your IP address is. This is not easy if your IP address is dynamic, like most people's are, because you will have to keep telling everyone what your current IP address is (comparable to changing your phone number every day). With a dynamic DNS service, like DtDNS.com, DynDNS.org, NO-IP.com and 2myDNS.com, you can get a static name to attach to that ever-changing IP address. Now, you just give out your static hostname instead of your IP address, and only tell the service what your IP address is. This way everyone will be able to find you quickly when you are online.
Dynamic IP Update Service automatically updates your IP at the dynamic DNS service everytime it changes. It is implemented as a reliable, managed Windows Service... |
|
Results in Tags For stealth ip
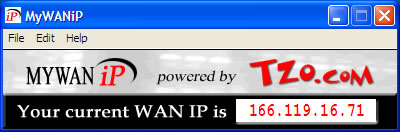 | MyWanIp is a Windows 95,98, ME, NT4, 2000 and XP utility that allows you to discover your WAN IP address. Many home and small business users have broadband routers like the Linksys, D-Link, SMC, Netgear, Cisco, Agere and others between their LAN and their Internet connection. When a LAN PC is connected behind one of these routers, most IP Address utilities will only tell you the LAN IP or private IP address. This is not useful to someone trying to connect to your router or your computer from the Internet. MyWanIP always displays the proper WAN IP Address - the TRUE IP address needed to connect to any PC on the LAN. MyWanIP uses remote servers to determine the Cable/DSL router's true WAN IP address, and shows that IP address in a small window. This allows you to determine the IP address that someone else needs to connect to your computer over the Internet. You can also COPY the displayed IP address into the clipboard for use in an email message... |
|
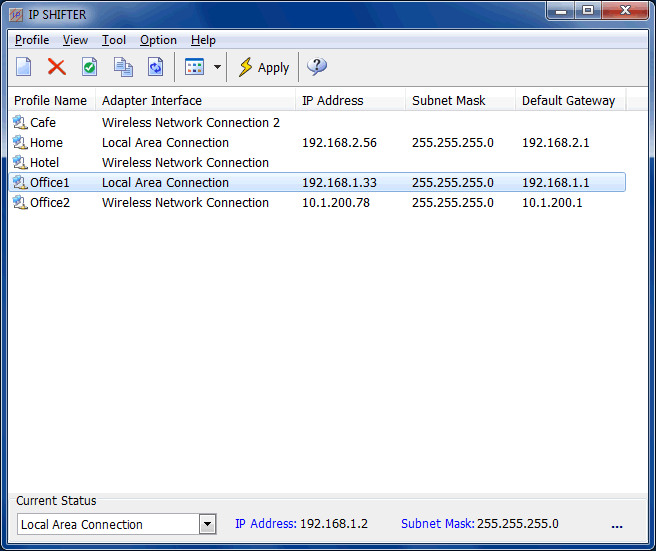 | If you work in different locations, or use your computer in more than one network, in these cases, you have to change your IP address parameters (e.g. IP address, Subnet mask, Gateway, DNS, Proxy) frequently, so this is a product for you!..
|
|
 | IP Detective Suite is an IP monitoring program that reports your changing IP address
to your ftp site, e-mails it to you and displays it on your desktop. This makes a perfect
tool for remote connection with programs such as pcAnywhere. IP Detective Suite inlcudes
IP Detective Original IP Publisher, IP e-mail alert and IP Desktop Viewer with copy to
clipboard function. Publisher stores changind ip address to any computer you wish and
publishes them in a list using IP Publisher. Monitor an unlimited number of ip addresses.
Access a published list from any computer... |
|
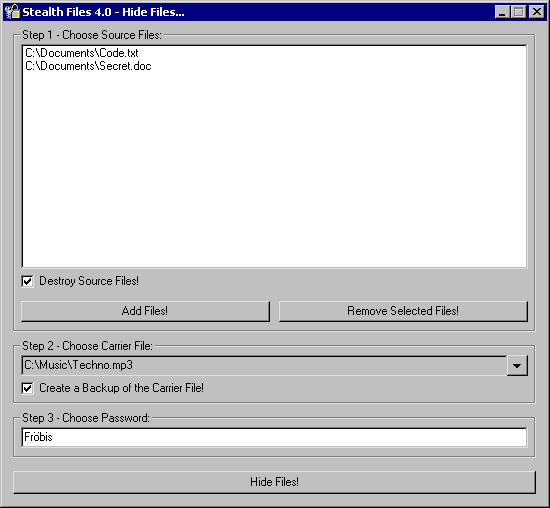 | Stealth Files hides any type of file in almost any other type of file. This is called steganography. This is a way of encrypting data so that it is hard to find. You can not decrypt something unless you know what to decrypt. Using steganography, Stealth Files compresses, encrypts, and then hides any type of file inside many other types of files, including EXE, DLL, OCX, COM, JPG, GIF, ART, MP3, AVI, WAV, DOC, BMP, and most other types of video, image, and executable files. You will still be able to view, open, and run these files without and problems. If you want to, you can also use a password to encrypt the hidden files...
|
|
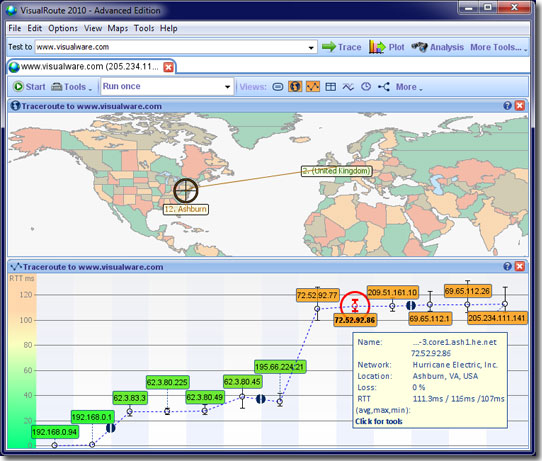 | VisualRoute combines several essential network tools to analyze Internet connections and identify bottlenecks that cause slow response. The path of each connection is shown on a world map, domain and network Whois lookups enable quick reporting... |
|
 | Stealth wars, you can't be seen, avoid cameras, guards, and security lasers...
|
|
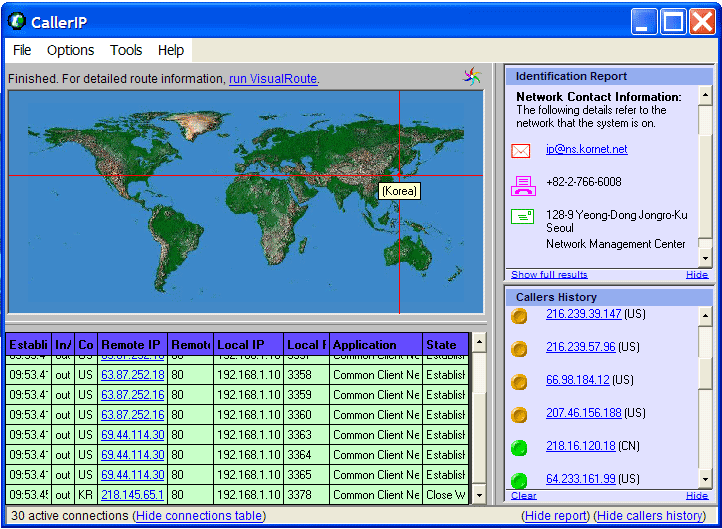 | CallerIP monitors activity on open ports on your system, which are often not protected by firewalls, and identifies backdoors that could allow harmful Trojans to steal your information. Connections are monitored in realtime and identified by country, a click on an IP address shows the city and country location on a world map. Worldwide WHOIS lookups show domain and network registration contact information, including abuse reporting information.
Connections to your system are provided in real-time, including the connection time, remote and local IP address, country of origin, remote and local ports being accessed. For Windows XP systems, the process ID is also identified, which helps determine if it is a legitimate process or may be harmful. A simple click on an IP address shows you where the connection originates on a global map, along with domain and network registration information.
CallerIP actively scans the ports on your system and alerts you to any backdoors or active HTTP/FTP/SMTP services, which could allow a harmful Trojan or enable unauthorized access to your system... |
|
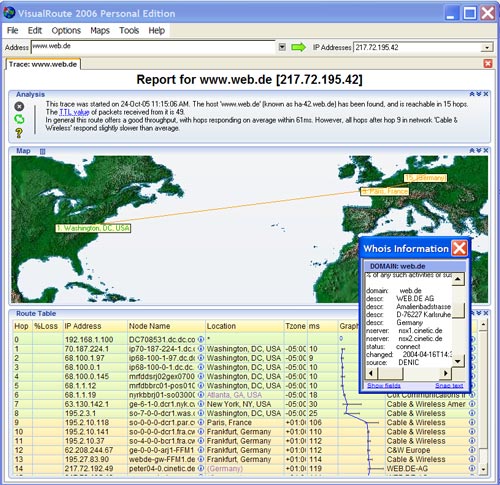 | VisualRoute combines the tools Traceroute, Ping, and Whois into an easy-to-use graphical interface that analyzes Internet connections to quickly locate where an outage or slowdown occurs. In addition, VisualRoute identifies the geographical location of IP addresses and Web servers on a global map--key information for security purposes to help identify network intruders and Internet abusers.
VisualRoute also features an email tracking for troubleshooting email problems, domain and network Whois information for quick problem or abuse reporting, and integration with Internet Explorer for one-click traces to any Web site. Several new edition options provide advanced tracing options, such as reverse tracing and remote tracing via a web browser, port testing and application availability testing.
The ping capabilities provide a good idea of whether or not the site is live, while traceroute will help determine where along the route the problem lies. VisualRoute's traceroute provides three types of data: an overall analysis, a data table, and a geographical view of the routing. The analysis is a brief description of the number of hops, where problems occurred, and the type of Web server software running at the site you are trying to reach. The data table lists information for each hop, including the IP address, node name, geographical location and the major Internet backbone where each server resides. The World map gives a graphical representation of the actual path of an Internet connection. Users can zoom in/out and move the map around to position it as desired. A mouse click on a server or network name opens a pop-up Whois window, providing instant contact information for problem reporting... |
|
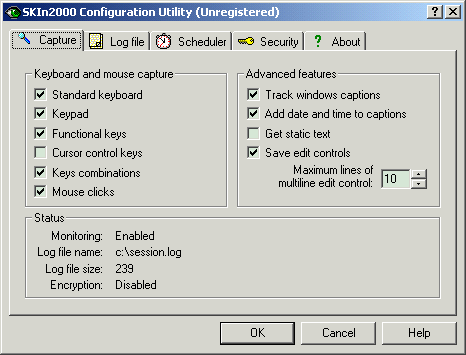 | Stealth Keyboard Interceptor for Windows NT/2000/ XP (SKIn2000) is a monitoring program which allows to intercept all keystrokes, mouse clicks, captions of active windows, static text and other... |
|
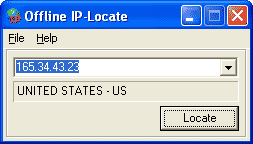 | Offline IP-Locate is a simple utility, which allow easy and quickly convert IP-address to country where this host located. Offline IP-Locate allow do it with out connecting to Internet... |
|
Related search : detective suite,stealth files,files stealth filesstealth files stealthinformation for,stealth wars,1000 stealth wars,information for,visualroute 2006 visualrouteinterceptor forkeyboard interceptorstealth keyboard,stealth keyboard interceptor,Order by Related
- New Release
- Rate
stealth action -
stealth seo -
stealth keyspy 2.0.0 -
stealth recorder 2.1 -
stealth aircraft -
|
|




























