|
|
Order by Related
- New Release
- Rate
Results in Title For secure hash
 | Simple logic game.
You do steps serially with the computer.
For the least number of steps you should grasp more blocks.
After you will choose color, the blocks of this color will adjoin your territory.
The field has the sizes 54x45 of blocks, total 2430 blocks, therefore for a victory you should grasp more than 1215 blocks. .. |
|
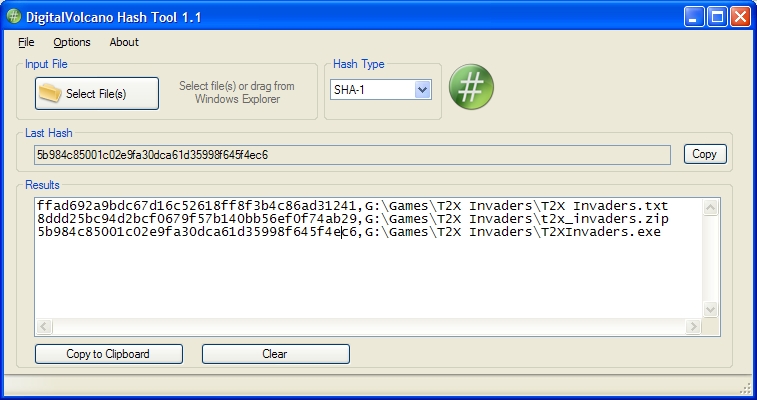 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface. ..
|
|
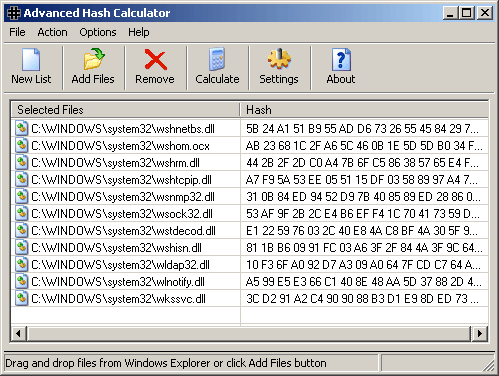 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2 .. |
|
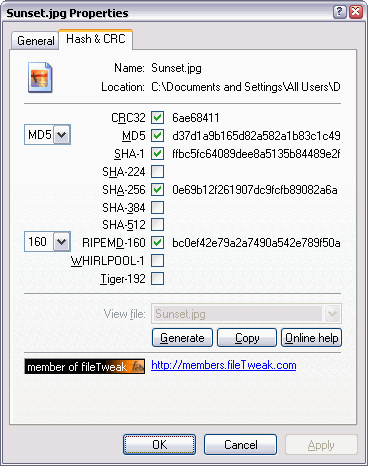 | Simple and easy to use file hash value calculator embedded into Windows properties pages and compatible with febooti fileTweak module integration. Supports CRC32, MD5, SHA-1 and other most common hash algorithms. ..
|
|
 | Have you ever tasted a sip of Safety ? If No then here is chance for it.Get the best Firewall that your system can get so that it remains in the ownership of yours.In this version you can also encrypt your files and safe gaurd them with a password. .. |
|
 | Secure-It is a local Windows security hardening tool, proactively secure your PC by either disabling the intrusion and propagation vectors proactively or simply reduce the attack surface by disabling unimportant functions. It secures Windows desktop PCs and Internet servers against new dangers by blocking the root cause of the vulnerabilities exploited by malware, worms and spy ware .
In some cases Secure-it is even able to protect your PC against threats prior to a patch release of the vendor.
* Harden your Local Zone Security (My Computer) settings.
* Proactively disable scripting or Active-X controls which proved potential propagation vectors in the past.
* Reduce potential intrusion vectors by disabling non used services.
* Various other protections. ..
|
|
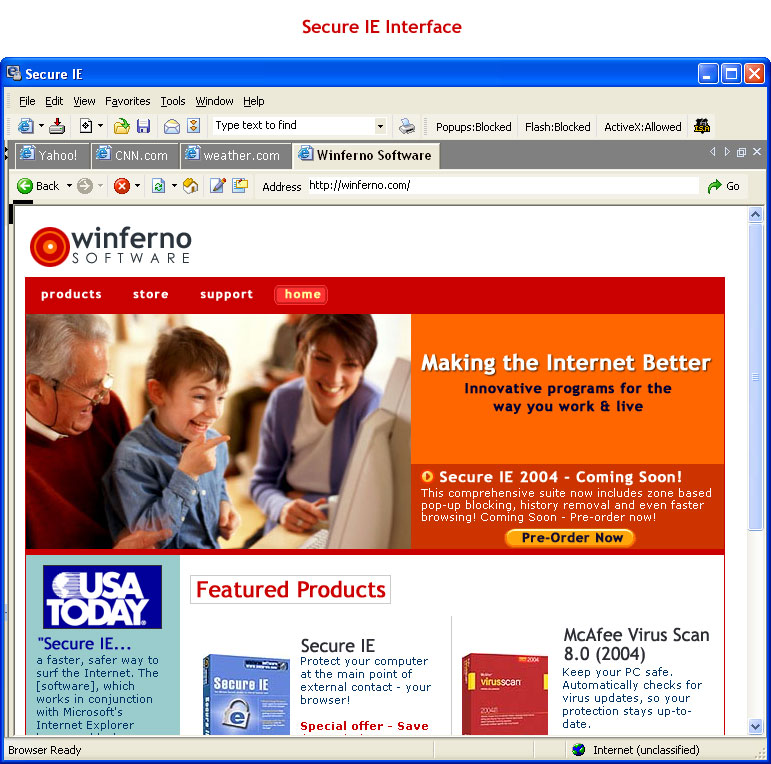 | Stop Hackers in Their Tracks!
Browse Safer and Faster with Secure IE
Imagine surfing up to a dozen Web sites at once without worrying about security threats, cookie spying, or being bothered by annoying popups.
Be SAFE and SECURE with Secure IE and turn your Web crawling into safe, turbocharged Web browsing!
Secure IE:
Stops Nasty Web Tricks
Safely and intelligently blocks unauthorized popups, protects your Favorites from unauthorized access, and also protects your browser from being 'hijacked' by hackers or unauthorized third parties.
Blocks Annoying Popup and Popunder Ads
Blocks unauthorized popup and popunder advertisements so that you can browse hassle free.
Protects Your Privacy
Set Secure IE to reject cookies from all but trusted sites - which you define. Never again worry about leaving credit card information, email addresses, passwords, and other personal information exposed to hackers.
Intercepts Malicious File Downloads
Secure IE intercepts all file downloads and virus-scans all file downloads (requires McAfee VirusScan).
Speeds Up Web Browsing
Browse faster with Secure IE's automatic Internet connection optimizations.
Features Sticky Notes and a highlighter
Make notes and highlight your favorite sections of Web pages.
Saves complete Web pages
Save even secure server (https) pages and archive your online transaction receipts.
Automatically tunes browser settings
For dial-up or broadband (Cable, DSL, T1). .. |
|
 | Keep your PC running faster, cleaner, and secure with IE Secure Mastera .. |
|
 | CD Secure prevents pirated copying and unapproved accessing your sensitive files and data in compact disk. .. |
|
 | SecureDisk is a program which can create encrypted virtual disks on Windows operation systems to protect your files or data from been accessed by others. .. |
|
Results in Keywords For secure hash
 | Send and receive secure and anonymous email. Backup, store and share files online securely. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface. HIPAA and GLBA compliant... |
|
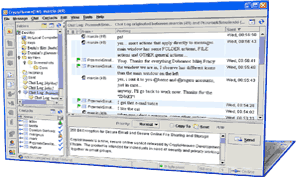 | Send and receive secure and anonymous email. Backup, store and share files online securely. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface.
Communicate and collaborate with your co-workers and friends accross networks and firewalls with very high level of security without a need for expensive VPN, PKI or complicated network administration, setup and maintainance. Formally comply with privacy and security provisions of: HIPAA, GLBA, SEC 17a-4; NASD 3010
2048 to 4096 bit Asymmetric and 256 bit Symmetric Key Encryption, Automatic Key and Contact Management.
Your data and your information stored in our Secure Data Center are illegible to anyone without your private key and passphase...
|
|
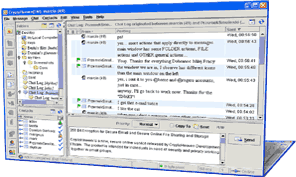 | Send and receive secure and anonymous email. Backup, store and share files online securely. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface.
Communicate and collaborate with your co-workers and friends accross networks and firewalls with very high level of security without a need for expensive VPN, PKI or complicated network administration, setup and maintainance. Formally comply with privacy and security provisions of: HIPAA, GLBA, SEC 17a-4; NASD 3010
2048 to 4096 bit Asymmetric and 256 bit Symmetric Key Encryption, Automatic Key and Contact Management.
Your data and your information stored in our Secure Data Center are illegible to anyone without your private key and passphase... |
|
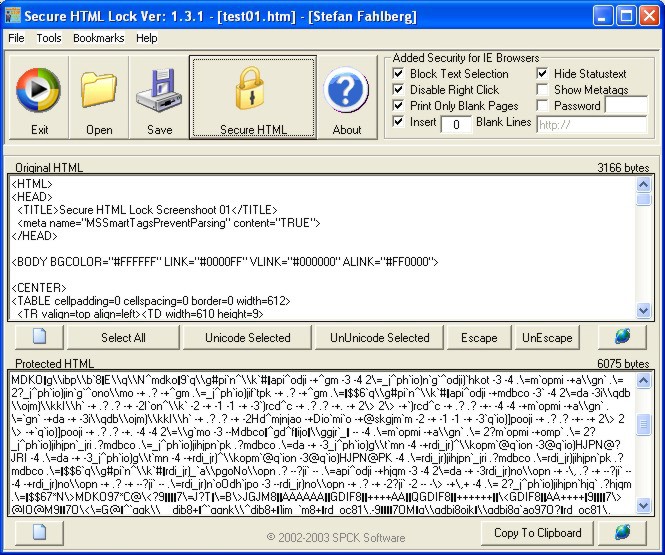 | Lock html, cryptate and protect your webpages from theift! Make your website secure and prevent theft of your html source code. Easy and fast to use, no html knowledge needed...
|
|
 | Secure your Web browser, your IM client, your Web e-mail, and your wireless connection with MySecureISP.com. Browse the Web safe and secure from insecure wireless hotspots, hackers trying to snoop your Web connection, ISPs selling your personal information, and ad tracking sites... |
|
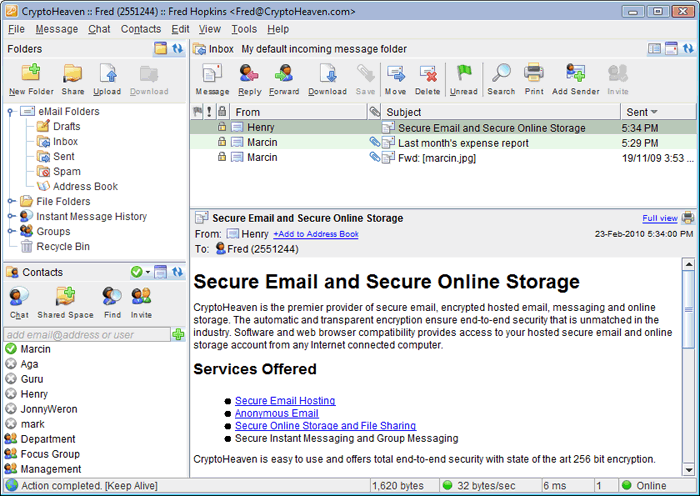 | Secure email with encrypted hosted storage. Chat and instant messaging for individuals and work groups in a secure and encrypted environment. Online file storage and document sharing via transparent AES encrypted platform. HIPAA and GLBA compliant...
|
|
 | Send and receive secure and anonymous email. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface... |
|
 | Send and receive secure and anonymous email. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface... |
|
 | Send and receive secure and anonymous email. Chat and exchange secure instant messages, create secure message boards. Share document folders through easy to use interface... |
|
 | QuantaMail is an e-mail enhancement that utilizes an existing e-mail service and provides secure, encrypted e-mail with message destruction and password-protection capabilities. After installing QuantaMail, one can immediately begin sending secure, encrypted email. Recipients of the secure mail will always be provided with a FREE QuantaMail viewer. Essentially QuantaMail gives the user complete control over their emails. Emails can never be opened without the necessary passwords, forwarded without consent, and can even be destroyed – before or after – it has been read. .. |
|
Results in Description For secure hash
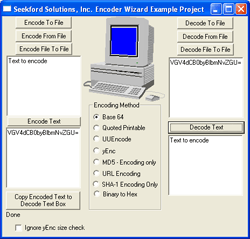 | Encoder Wizard is a collection of two ActiveX (ocx) controls, Encoder Wizard and Decoder Wizard. These two controls allow you to fully support the Base64, Quoted- Printable, UUEncode, yEnc, MD5,HMAC MD5, URL, SHA-1, and Binary 2 Hex encoding methods. You can Encode and Decode data quickly and intelligently. Base 64 is the Encoding Method usually used for Binary files in MIME messages. It is also used to encode data for special characters accross telnet connection to certain servers. Quoted-Printable is used to encode text for transmission accross certain mail servers. It is also commonly used in MIME messages. UUEncode is the data encoding mechanism used by Unix systems for encapsulating binary data so that it can transported safely accross network connections. yEnc is a recently created encoding method that is now used a lot in newsgroups since it is significantly more efficient for data storage than the UUEncode format. yEnc takes advantage of being able to use 8 bit encoding as opposed to the more restricted form of 7bit encoding used by UUEncode. MD5 is a message digest hash algorithm that is used for validation and verification of message integrity. It creates a highly unique 16 byte ( 128 bit ) digest from a set of data that is almost impossible to recreate without the same exact input data. HMAC MD5 is also supported. This allows for a "keyed" hash algorithm. The hash will only generate the same value when the data and key are the same. Great for integrity checks and secure hash generation. SHA-1 is another highly secure message digest algorithm used by the United States Government. It is now a publicly open algorithm which uses a 160 bit or 20 byte digest. The hash from any set of data less than 2^64 bytes in length provides a unique hash that is only creatable by the unique byte order... |
|
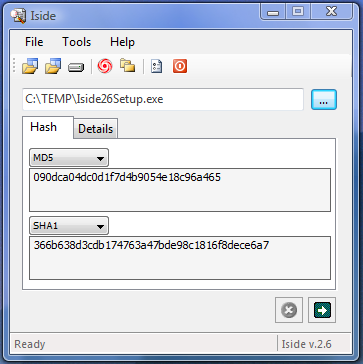 | Iside is a message digest, hash code computing tool. It can be used for file integrity checking. It also compares files and folders by computing their hash code (MD5,SHA1,CRC32,...)...
|
|
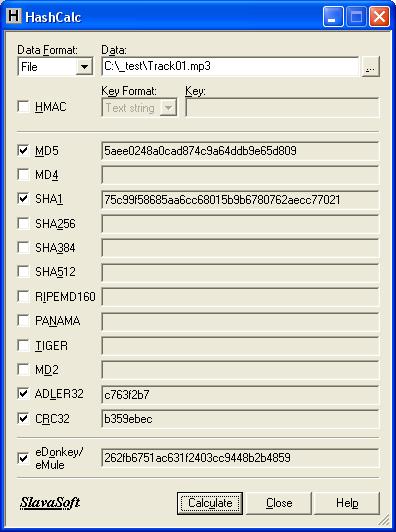 | Fast calculator to compute hash, checksum, HMAC values for file, text and hex string. Supports MD2,MD4,MD5, SHA1,SHA2, RIPEMD160,PANAMA,TIGER, CRC32,ADLER32 algorithms and the hash used in eMule/eDonkey(eDonkey2000,ed2k). Good to check/compare files... |
|
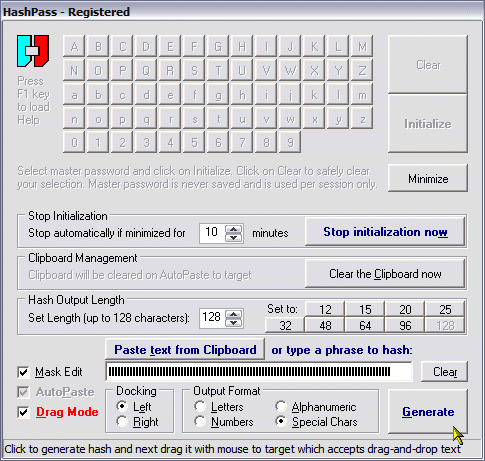 | HashPass is a password generator that revolutionizes the way you use your passwords. Based on your individual and safely entered criteria, it mathematically transfers your password-to-be into a unique secure hash which becomes your real password...
|
|
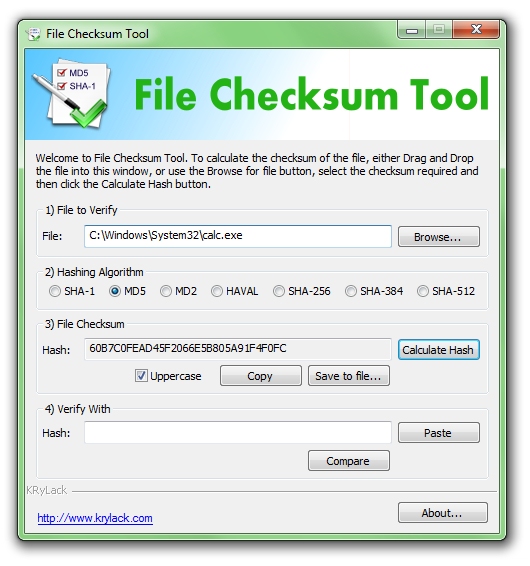 | File Checksum Tool is a free utility that calculates MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512 hash from a file. The software allows you to verify the Hash or create new checksum for your important data... |
|
 | Data Fortress has been almost completely rewritten and has a totally new look! Features include: a new intuitive interface, quick floppy encrypt feature, save encrypted list(s) of important files for quick cyphering, error-logging, and wipe-out feature. Data Fortress can be used on files, folders and entire drives. Registered users enjoy using Data Fortress.s high security cypher Blowfish in its most secure mode (CBC) with a unique IV. Data Fortress can even tell if the input password is correct using a secure one-way hash function! ..
|
|
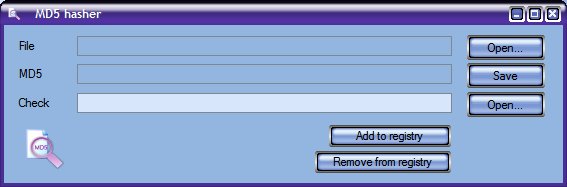 | Computes MD5 hash for any single file, can compare it with given. Integrates in Send To and shell on demand. Un-integrates on demand. Drag-and-drop supported. Automatically looks for corresponding md5 file with hash to compare, and vise-versa... |
|
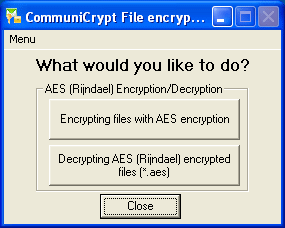 | File encryption/decryption tools with strongest AES algorithms. Can generate the hash of the source file as password for symmetric encryption(64 digits password).
Encryption strength AES Rijndael: 256 bit / Hash: SHA-256.. |
|
 | Need to upload website updates daily? Try FTPGetter: a secure FTP automation scheduler. FTPGetter has a unique feature of using wildchars for processing files by mask. Compare files by modification date, MD5 hash and upload only new/modified files... |
|
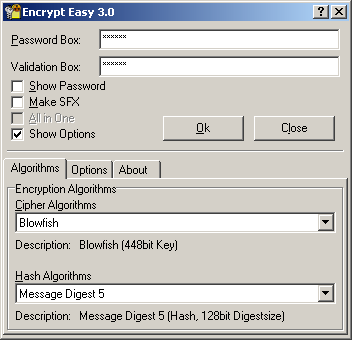 | Encrypt Easy is a highly secure file encryption program. Current version of Encrypt Easy uses the 67 encryption methods: Cipher: 3Way, Blowfish, Gost, IDEA, Q128, SAFER-K40, SAFER-SK40, SAFER-K64, SAFER-SK64, SAFER-K128, SAFER-SK128, SCOP, Shark, Square, TEA, TEA extended, Twofish, Cast 128, Cast 256, DES Single 8byte, DES Double 8byte, DES Double 16byte, DES Triple 8byte, DES Triple 16byte, DES Triple 24byte, DESX, Diamond II, Diamond II Lite, FROG, Mars, Misty 1, NewDES, RC2, RC4, RC5, RC6, Rijndael, Sapphire II, Skipjack. Hash: Message Digest 4, Message Digest 5, Secure Hash Algorithm, Secure Hash Algorithm 1, Ripe Message Digest 128, Ripe Message Digest 160, Ripe Message Digest 256, Ripe Message Digest 320, Haval-128, Haval-160, Haval-192, Haval-224, Haval-256, Sapphire II-128, Sapphire II-160, Sapphire II-192, Sapphire II-224, Sapphire II-256, Sapphire II-288, Sapphire II-320, Snefru-256, Square, Tiger, XOR-16, XOR-32, CRC-16 CCITT, CRC-16 Standard, CRC-32. Each file is encrypted with two encryption methods, Cipher+Hash, and with its own password and can only be decrypted using the same password. This version also has self extracting. Now you can send encrypted files through Internet and decrypt them without using Encrypt Easy program. It is very fast, comfortable and safe! New version of Encrypt Easy gives user even more functions - better interface, encrypted file compression, command line tool, Windows XP support, password validation box, detailed description of all function, interactive demonstration for users. .. |
|
Results in Tags For secure hash
 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2.. |
|
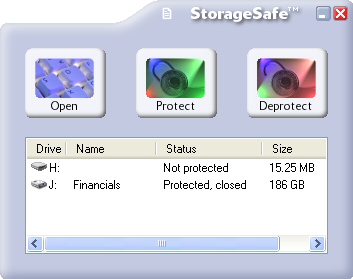 | StorageSafe provides high performance security for flash and hard disk type storage on USB and IEEE 1394 buses. It includes transparent device encryption, guards against 180,000+ common passwords, and secure file and device erase.
From the ground up, StorageSafe was designed to meet end-user demands such as 1) genuine security; 2) solid reliability; 3) everyday ease-of-use, and; 4) little or no reduction in productivity.
After the device password is entered, the 256-bit Advanced Encryption Standard, the 512-bit Secure Hash Algorithm, and others from our time tested media security library go to work, silently. There is no noticeable impact on bandwidth, even with older generation CPUs. An extensible system instantly checks for and limits the use of more than 180,000 common (easy to guess) passwords. Secure file and device erase that exceeds DoD Standards can remove sensitive files from unwanted locations.
All commands except (Install/Uninstall) work under Windows Guest/Limited User accounts. As another industry first, the deprotect routines are fully interrupt tolerant. This is especially important given that the product is targeted at devices that can be detached at any time.
StorageSafe is licensed by CPU, not by device. Therefore, it cost effectively provides a unified security interface to your entire inventory of USB/IEEE 1394 storage devices.
The single unit, direct download price is $24.99; multi-unit pricing and site licenses are available. To ensure your complete satisfaction, we include a 30-day Money Back Guarantee...
|
|
 | SHA-1 Password is a tool for security professionals, which allows recovering a password if you know its SHA-1 hash. The fast recovery engine can recover up to 32,000 passwords simultaneously... |
|
 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest...
|
|
 | SoftFuse Password Generator Std is a program for generating strong passwords with a single mouse click! Start quickly create strong secure passwords for your e-mail account, instant messenger, your computer system and web sites!.. |
|
 | SoftFuse Password Generator Std is a program for generating strong passwords with a single mouse click! Start quickly create strong secure passwords for your e-mail account, instant messenger, your computer system and web sites!..
|
|
 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface... |
|
 | NCP Secure Entry Client for communication with any IPSec gateway (compatibility list at http://www.ncp.de). The Client supports Windows CE, incl. Mobile 5, and any wired or wireless network. A personal firewall is included... |
|
 | NCP Secure Entry Client for communication with any IPSec gateway (compatibility list at http://www.ncp.de). It supports all transmission networks as well as Windows operating systems and has an integrated Personal Firewall... |
|
 | NCP Secure Entry Client for communication with any IPSec gateway (compatibility list at http://www.ncp.de). It supports all transmission networks like ISDN, the analog network, xDSL, Internet, GSM, GPRS, IMTS, LAN, WLAN, and it runs under all Windows operating systems. A permanently integrated Personal Firewall shields the PC against attacks in all communication environments. All security mechanisms are already active when the system starts and they remain active until the Entry Client is deactivated. IP-NAT, Stateful Packet Inspection, defined filter rules, Friendly Net, and hotspot detection (automatic detection of the current network environment and activation of the corresponding filter rules). Authentication relative to the destination gateway can be executed via OTP tokens or certificates (soft certificates, smart cards, USB tokens) in a PKI, at your discretion. All data are encrypted for transmission. Support for: Triple DES 128, 192-bit, Blowfish 128-bit, AES 128, 192, 256-bit, and RSA 1024, 2048-bit. The Entry Client can also be implemented in IT environments without permanent IP addresses. DynDNS (Dynamic DNS) is used to dial-in to the central VPN gateway with changing public IP addresses which are queried via a public DynDNS server (prerequisite: the destination gateway must support DynDNS). As an alternative to the Microsoft RAS dialer the Entry Client has its own dialer which is operating-system independent. It offers the following advantages: telephone charge savings, handover and optimization of central VPN resources through intelligent Short Hold Mode, remote administration, and protection from outside dialers... |
|
Related search : message digestmd5 hash,securely than usuallysoftfuse password generator,securely than usuallysoftfuse password generatorhash sha,entry clientsecure entryncp secure,ncp secure entryentry clientsecure entryncp secure,ncp secure entryentry linux clientsOrder by Related
- New Release
- Rate
hash tables -
hash keys -
hash file -
hash downloader 1.0.0 -
hash values -
|
|
































