|
|
Order by Related
- New Release
- Rate
Results in Title For hash file
 | Simple logic game.
You do steps serially with the computer.
For the least number of steps you should grasp more blocks.
After you will choose color, the blocks of this color will adjoin your territory.
The field has the sizes 54x45 of blocks, total 2430 blocks, therefore for a victory you should grasp more than 1215 blocks. .. |
|
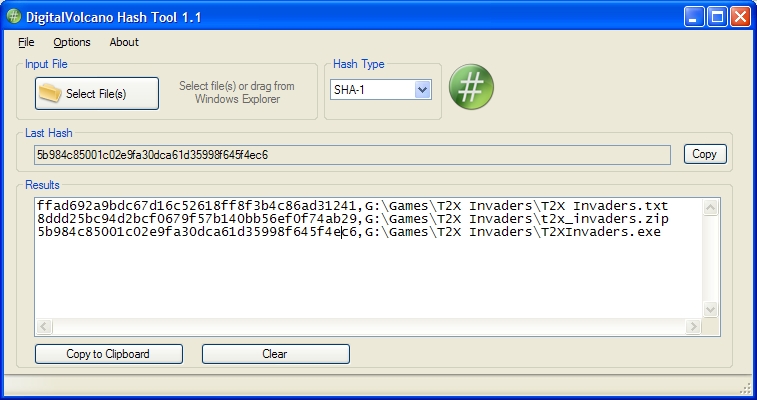 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface. ..
|
|
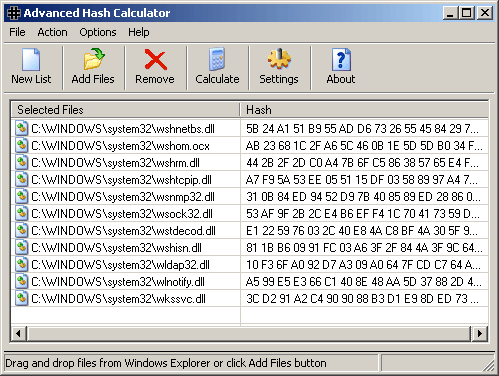 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2 .. |
|
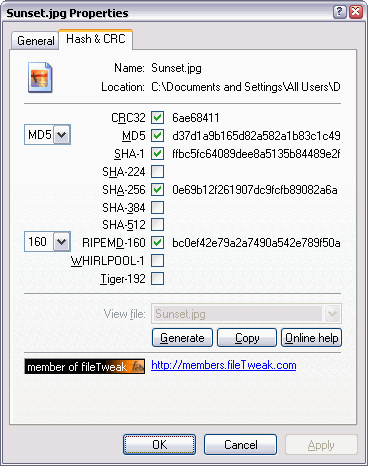 | Simple and easy to use file hash value calculator embedded into Windows properties pages and compatible with febooti fileTweak module integration. Supports CRC32, MD5, SHA-1 and other most common hash algorithms. ..
|
|
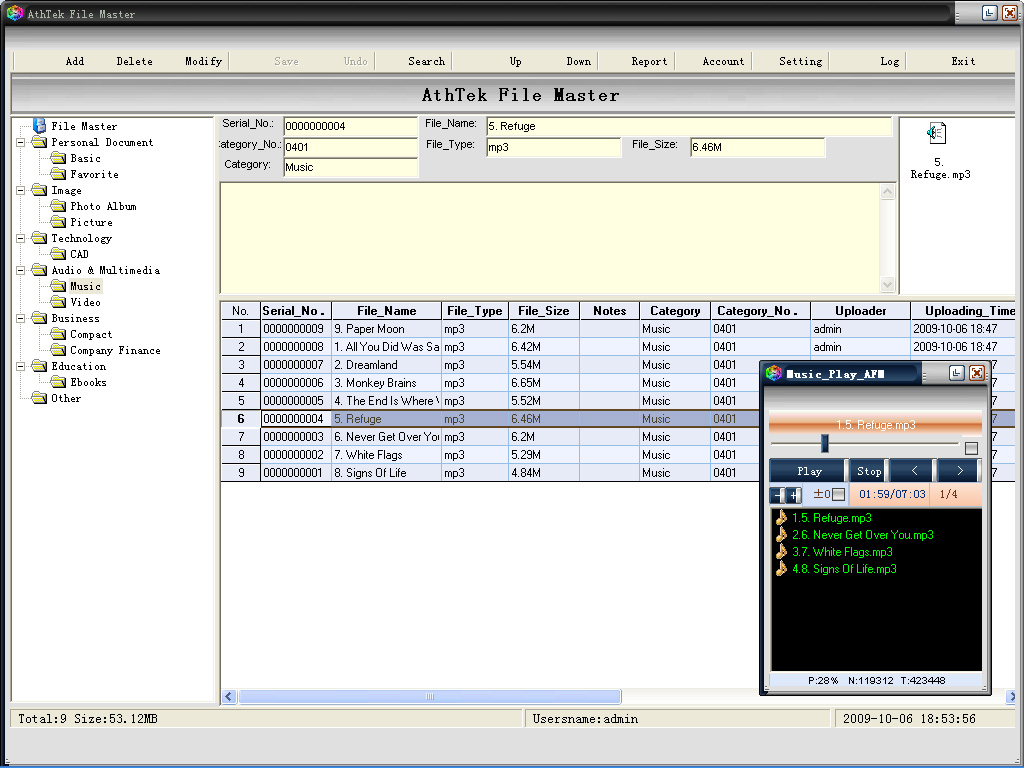 | As a new advanced file management tool, AthTek File Master is easy to use, efficient to supervise and secure to preserve. After installation, press F1 to read the Help File to learn how to use it. Your files are safety sync with AthTek File Master. .. |
|
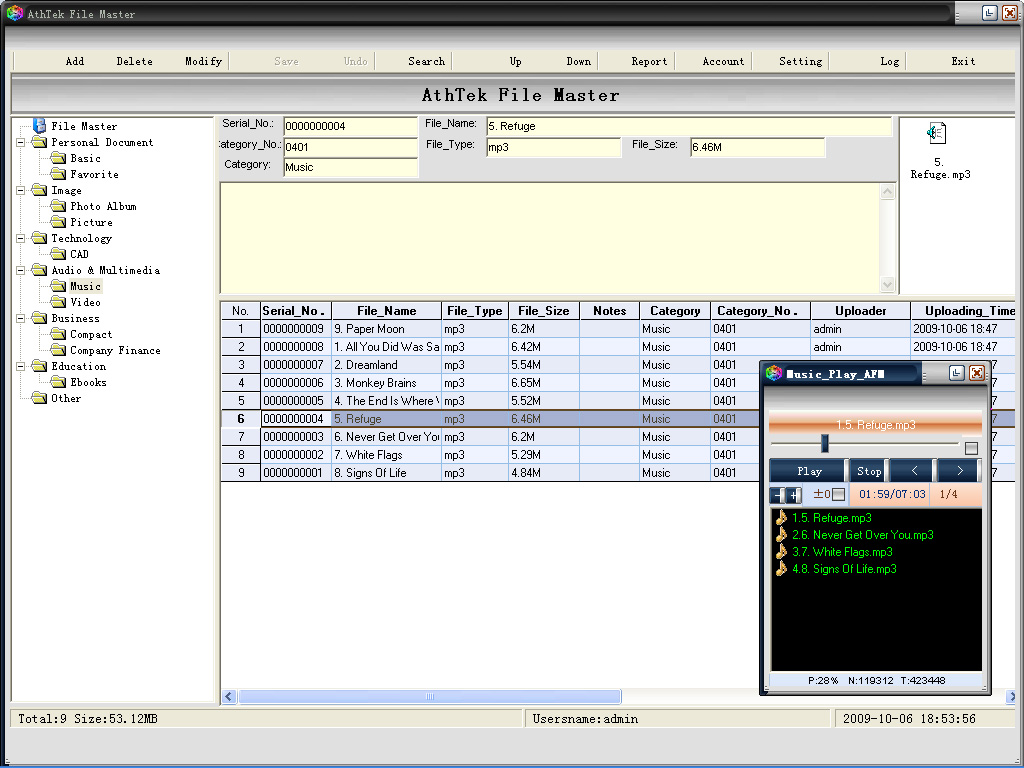 | As a new advanced file management tool, AthTek File Master is easy to use, efficient to supervise and secure to preserve. After installation, press F1 to read the Help File to learn how to use it. Your files are safety sync with AthTek File Master. ..
|
|
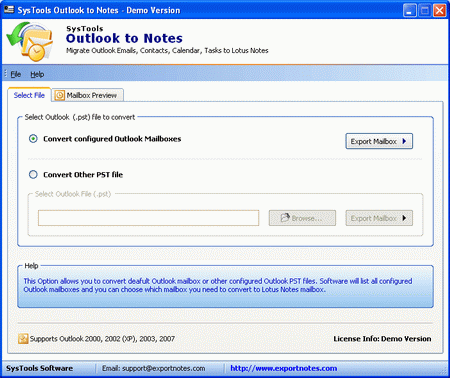 | The Outlook to Notes software by SysTools provides to Convert PST file to Notes File in the safest way possible. Transfer various configured and orphaned Outlook data (inbox, outbox, contacts, etc) with their meta-data, while Converting PST to NSF. .. |
|
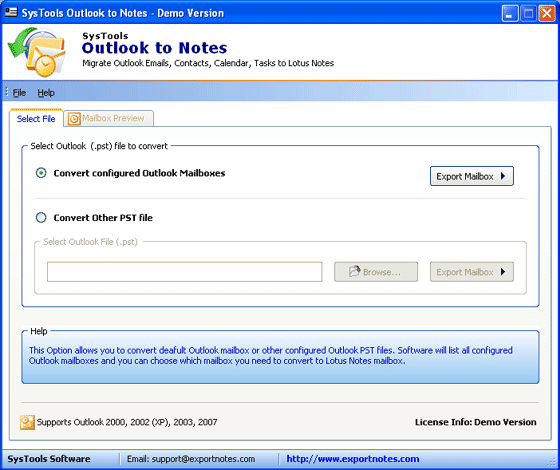 | How to Convert .PST to .NSF? SysTools offers the PST to NSF Converter to Convert Outlook PST File to Lotus Notes with its key element of email items (to, cc, etc), inbox, contacts, etc. Convert configured or orphan file of Outlook PST to Lotus Notes. .. |
|
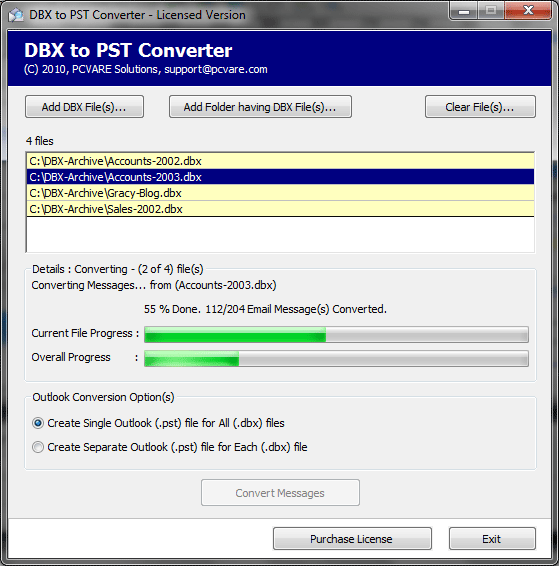 | Use DBX File to PST File Converter tool at PCVARE Solution to convert DBX file to PST file. DBx File to PST File Converter tool supports batch conversion feature to convert multiple DBX files at a time. .. |
|
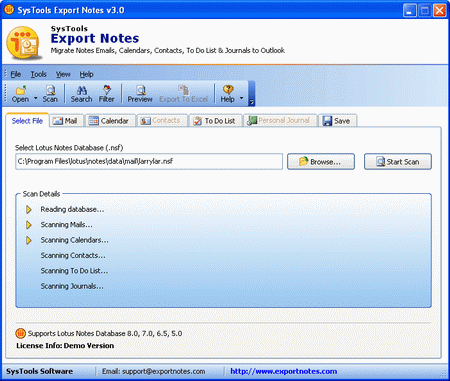 | Convert Lotus Notes to MS Outlook email with Convert NSF file to PST file conversion tool that convert domino server mailbox to Outlook. It convert Lotus Notes emails, calendars, contacts, attachments, sent items, journals, tasks etc to PST file. .. |
|
Results in Keywords For hash file
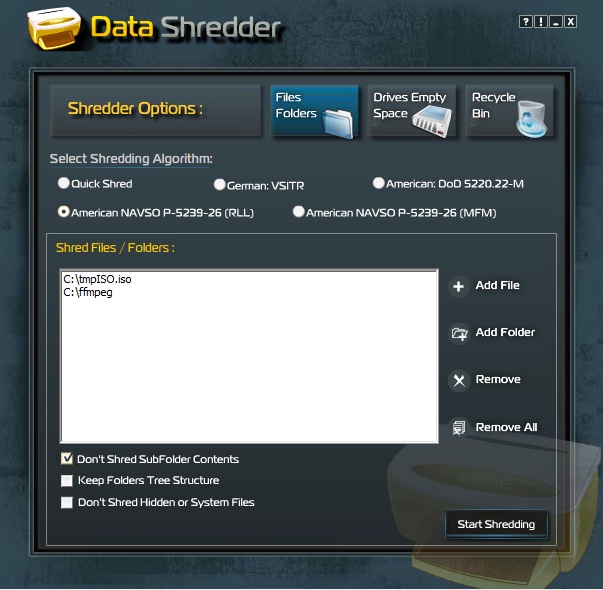
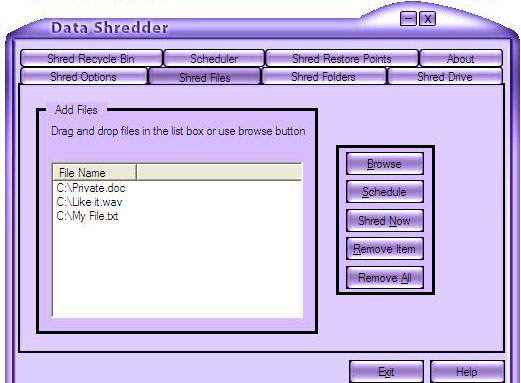 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
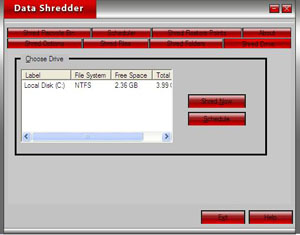 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered...
|
|
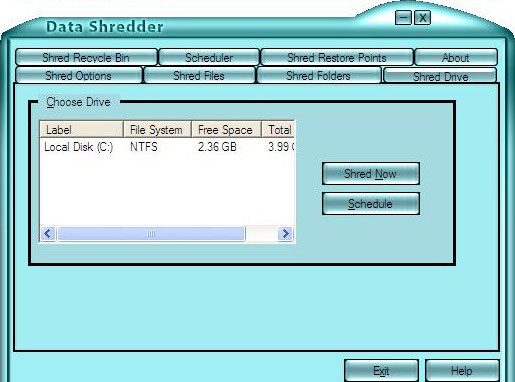 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
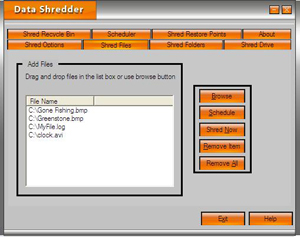
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered...
|
|
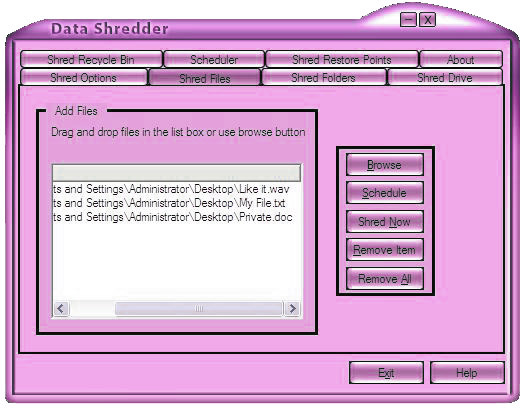
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
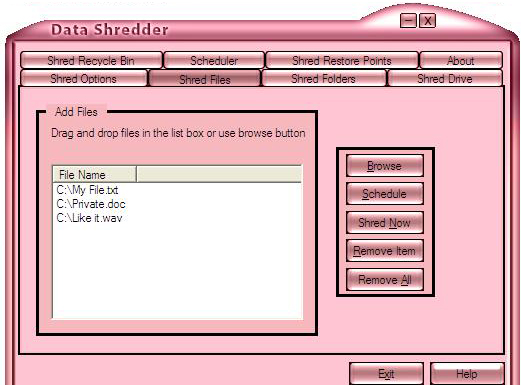
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered...
|
|
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
 | Data Shredder literally destroys files, free space and your Recycle Bin contents instead of only deleting them. That means your data contents once overwritten and destroyed It can`t be recovered... |
|
Results in Description For hash file
 | Iside is a message digest, hash code computing tool. It can be used for file integrity checking. It also compares files and folders by computing their hash code (MD5,SHA1,CRC32,...)... |
|
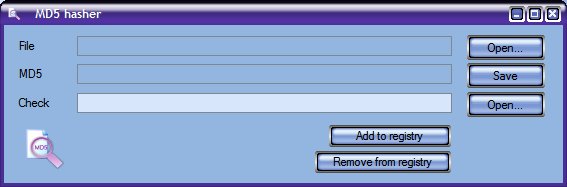 | Computes MD5 hash for any single file, can compare it with given. Integrates in Send To and shell on demand. Un-integrates on demand. Drag-and-drop supported. Automatically looks for corresponding md5 file with hash to compare, and vise-versa...
|
|
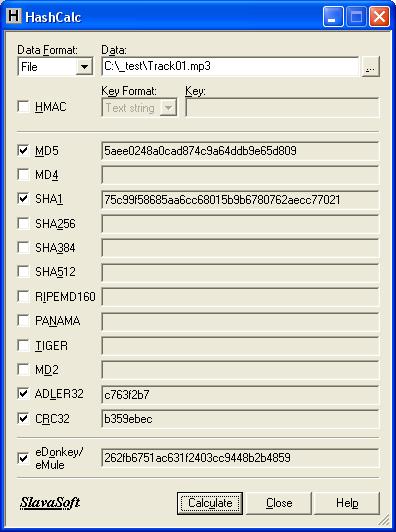 | Fast calculator to compute hash, checksum, HMAC values for file, text and hex string. Supports MD2,MD4,MD5, SHA1,SHA2, RIPEMD160,PANAMA,TIGER, CRC32,ADLER32 algorithms and the hash used in eMule/eDonkey(eDonkey2000,ed2k). Good to check/compare files... |
|
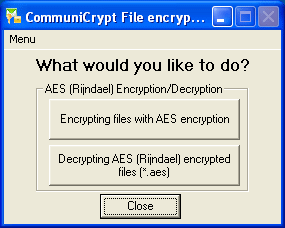 | File encryption/decryption tools with strongest AES algorithms. Can generate the hash of the source file as password for symmetric encryption(64 digits password).
Encryption strength AES Rijndael: 256 bit / Hash: SHA-256..
|
|
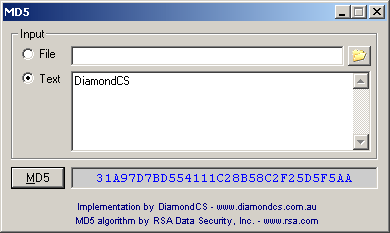 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest... |
|
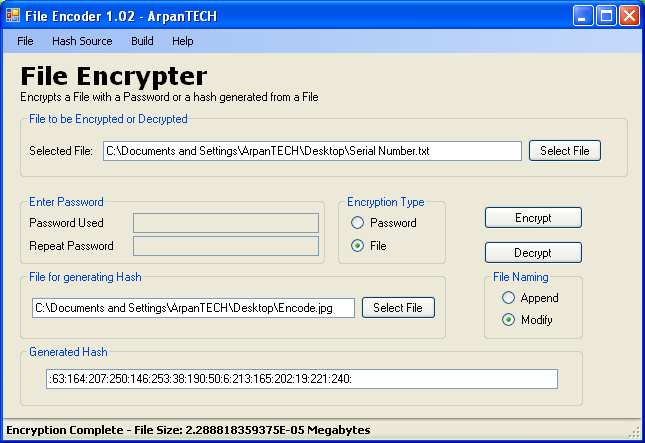 | Encrypts a given file using a password or a file used as a password. A hash is generated from the file or the password and then the file is encrypted with the generated hash...
|
|
 | Easy and advanced encryption, decryption and hash ActiveX component for ASP or ASP.Net
Support encryption and decryption of file, string, memory buffer
Support calculation of hash on string, file or memory buffer
Support digital signature.. |
|
 | Hyper Hasher is a small utility that allows you to calculate hash/checksum values for any file on your system, or text string. It combines the cryptography libraries built into the Microsoft .NET framework with the expansive Crypto++ cryptography library and other hashing libraries from around the internet.Features:-Hash Functions: MD2, MD4, MD5, SHA-1, SHA-256, SHA-384, SHA-512, HAVAL, Tiger, Panama, RIPEMD-160, FCS-16, FCS-32, GHash-32-3, GHash-32-5, GOST, Size32-Hash, emule/edonkey-Checksums: CRC16, CRC16-CCITT, CRC32, Adler32-Windows Shell Integration (optional)-Configuration Saving -Automatically compare two files.-Dump results to file.-Pentium 4 optimization.-Processor priority control. .. |
|
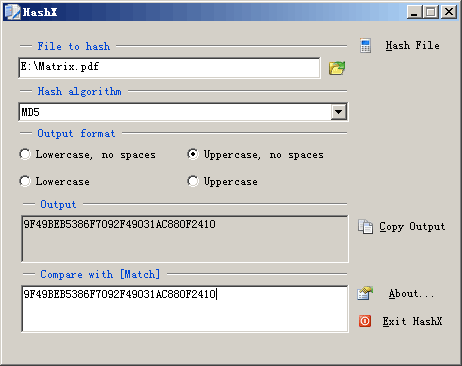 | HashX is a powerful yet very easy to use application designed for computes hash value(checksum) for any single file, it allows you to verify that downloaded files are not corrupted or otherwise unusable... |
|
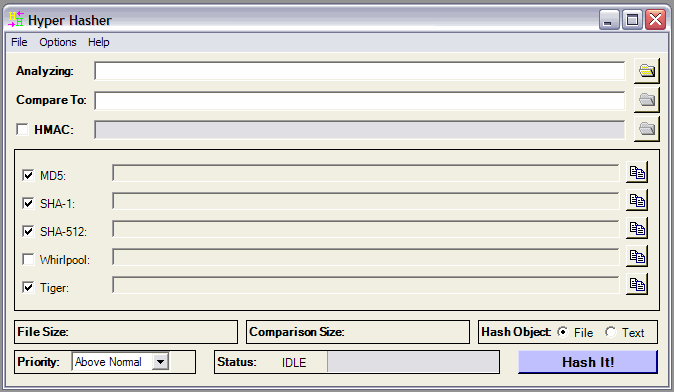 | The ultimate hashing utility! The Hyper Hasher Suite allows you to calculate 26 different hash/checksum and HMAC values for any file on your system, while the HashFile utility adds support for MD5 & SFV file creation and verification... |
|
Results in Tags For hash file
 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2.. |
|
 | Iside is a message digest, hash code computing tool. It can be used for file integrity checking. It also compares files and folders by computing their hash code (MD5,SHA1,CRC32,...)...
|
|
 | Encrypts a given file using a password or a file used as a password. A hash is generated from the file or the password and then the file is encrypted with the generated hash... |
|
 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest...
|
|
 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface... |
|
 | File verification utility, uses SHA-2 algorithm...
|
|
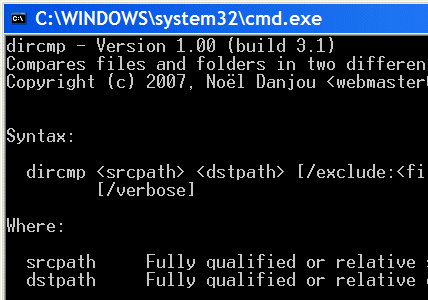 | DirCmp is a command-line tool that allows you to compare two directories and possibly their subdirectories. The program reports files missing in either directory and whether some files are different or empty... |
|
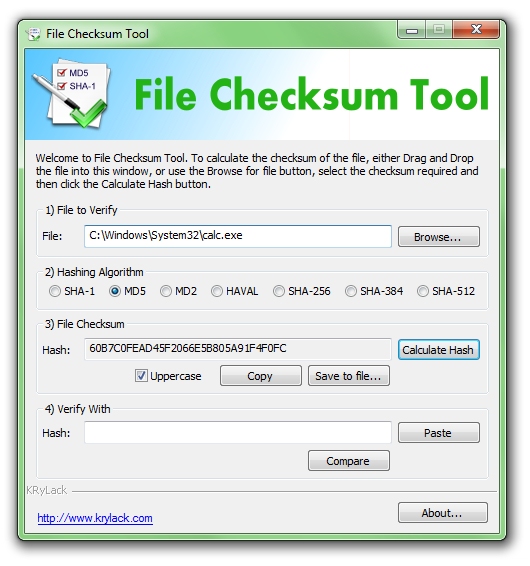 | File Checksum Tool is a free utility that calculates MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512 hash from a file. The software allows you to verify the Hash or create new checksum for your important data... |
|
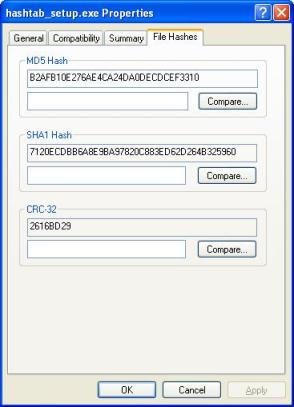 | A windows shell extension which installs a new tab with file hash information. Includes MD5, SHA1 and CRC032. Also allows for easy hash comparison. Great for verifying downloads without requiring any external tools... |
|
 | Easy and advanced encryption, decryption and hash ActiveX component for ASP or ASP.Net
Support encryption and decryption of file, string, memory buffer
Support calculation of hash on string, file or memory buffer
Support digital signature.. |
|
Related search : ash code,message digestmd5 hash,hash sha,,file checksum tool,encryption andalgorithm likesupport encryptionmd5 shahash algorithmultra cryptocrypto component,ultra crypto componentsha sha256 sha384sha256 sha384 sha512memory buffer supporthash algorithOrder by Related
- New Release
- Rate
hash plants -
hash algorithm -
hash generator -
secure hash -
hash cracker -
|
|
































