|
|
Order by Related
- New Release
- Rate
Results in Title For hash keys
 | Simple logic game.
You do steps serially with the computer.
For the least number of steps you should grasp more blocks.
After you will choose color, the blocks of this color will adjoin your territory.
The field has the sizes 54x45 of blocks, total 2430 blocks, therefore for a victory you should grasp more than 1215 blocks. .. |
|
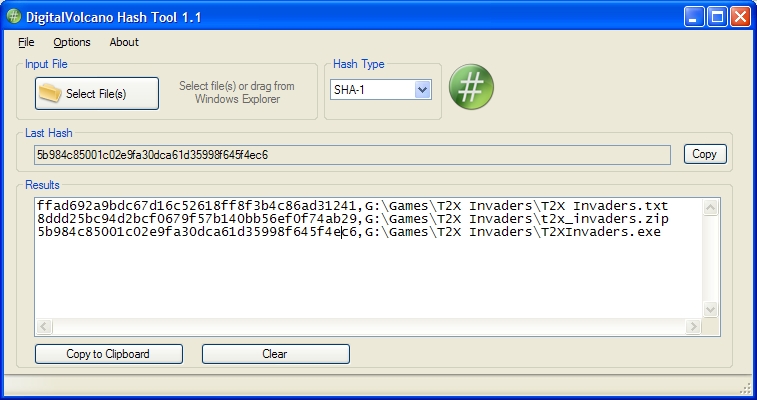 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface. ..
|
|
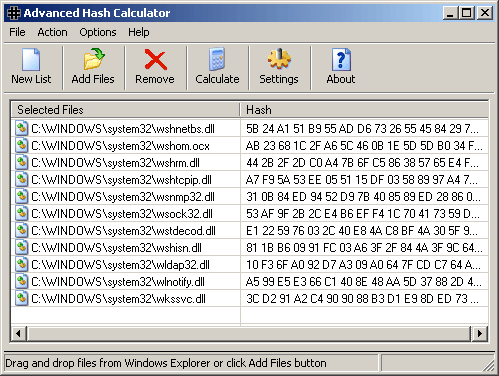 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2 .. |
|
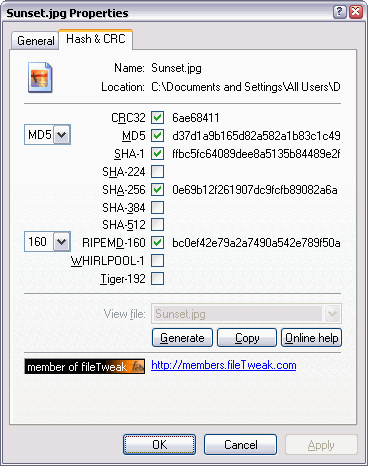 | Simple and easy to use file hash value calculator embedded into Windows properties pages and compatible with febooti fileTweak module integration. Supports CRC32, MD5, SHA-1 and other most common hash algorithms. ..
|
|
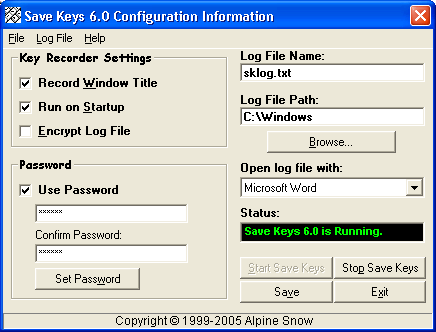 | Save Keys 6.0 is a completely invisible key recorder that secretly records every key typed into the keyboard along with the window title of the window or program that the keys were typed into. Save Keys 6.0 makes encryption of mail, messages, and passwords completely useless because these can be saved to file before they are encrypted. .. |
|
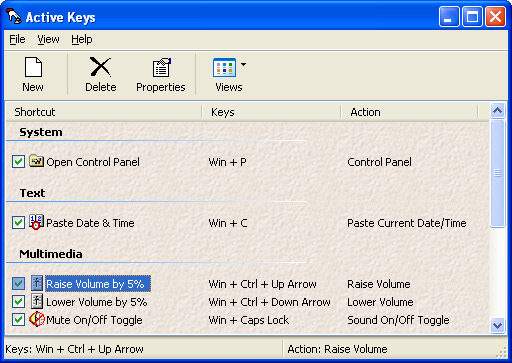 | Control sound settings and screen resolution, start screensaver, insert current time and date or custom text with just one key press! Create custom keyboard shortcuts for any action of your system! Turn your keyboard into a remote controller! ..
|
|
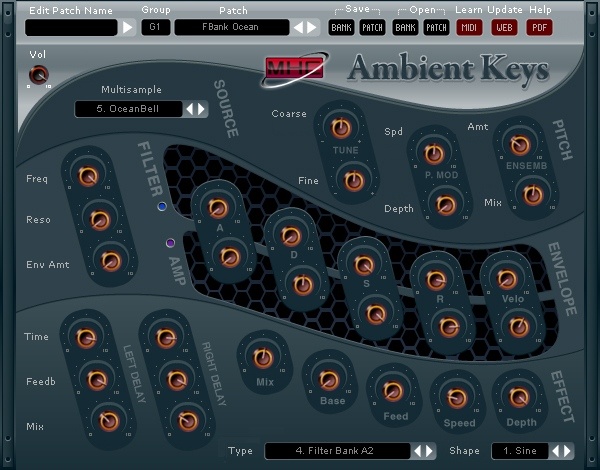 | Ambient Keys is one of MHC's vst plugins with an ambient sound, playing hundreds of ambient waveforms and processing these. .. |
|
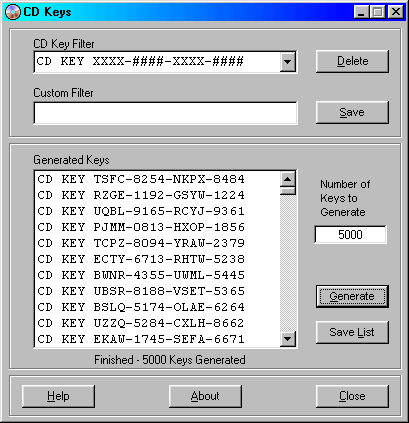 | Create from one to thousands of unique CD Key/Serial Numbers. Use 25 predefined filters or create your own. Each set generated will create the number of Keys you specify without any duplications. Save to file and print. .. |
|
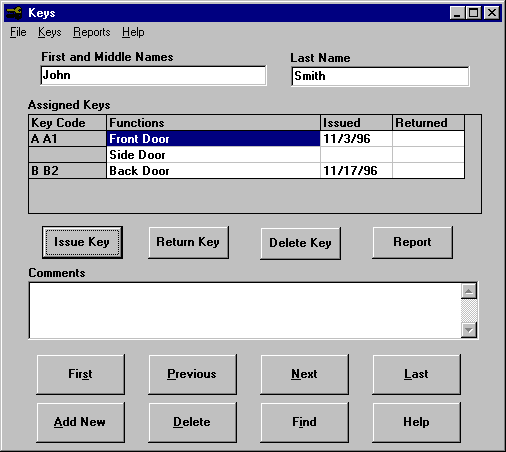 | The Keys Program is an easy to use database for businesses to keep track of keys for buildings, offices or vehicles that are issued to employees or other individuals. The program will keep a complete and permanent record of all key loans. .. |
|
 | Passwords & Keys is a powerful random number, password and key generator,that allows you to easily generate, store and use random passwords, keys and data.Passwords & Keys has four different generation methods (number, password, mask1, mask2).This program support templates and has handy password manager.It is compact, simple and easy to use. Try this powerful program. .. |
|
Results in Description For hash keys
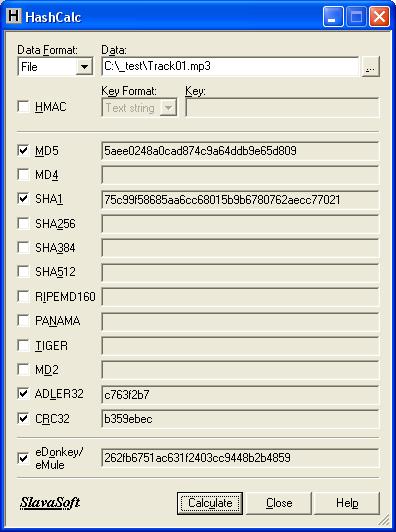 | Fast calculator to compute hash, checksum, HMAC values for file, text and hex string. Supports MD2,MD4,MD5, SHA1,SHA2, RIPEMD160,PANAMA,TIGER, CRC32,ADLER32 algorithms and the hash used in eMule/eDonkey(eDonkey2000,ed2k). Good to check/compare files... |
|
 | Easy to use typing activity capture program provides option to prepare reports of key pressed. Innovative key stroke catcher application monitors keys pressed like character keys, digit keys, symbol keys, and special keys like shift, control etc...
|
|
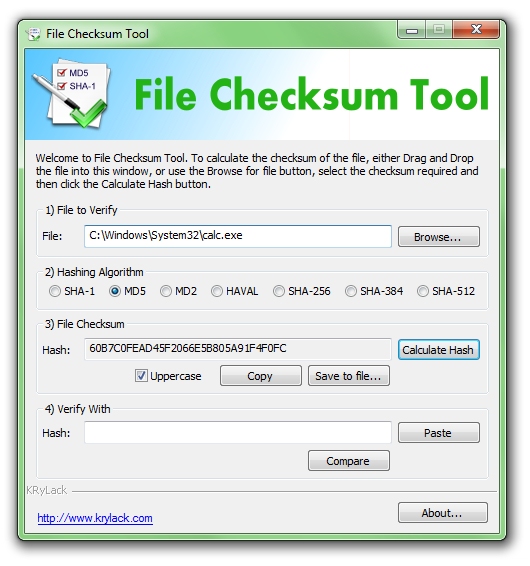 | File Checksum Tool is a free utility that calculates MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512 hash from a file. The software allows you to verify the Hash or create new checksum for your important data... |
|
 | Computes MD5 hash for any single file, can compare it with given. Integrates in Send To and shell on demand. Un-integrates on demand. Drag-and-drop supported. Automatically looks for corresponding md5 file with hash to compare, and vise-versa...
|
|
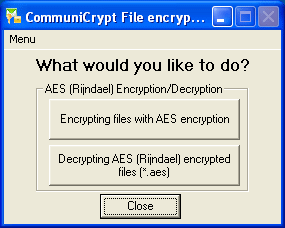 | File encryption/decryption tools with strongest AES algorithms. Can generate the hash of the source file as password for symmetric encryption(64 digits password).
Encryption strength AES Rijndael: 256 bit / Hash: SHA-256.. |
|
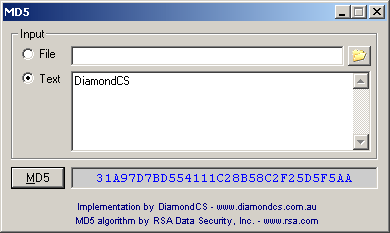 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest...
|
|
 | Protect your personal messages with encryption keys of your choice. Tthen give the keys to people you trust. - When or if the need arises, change the keys to ensure continued privacy. Outstanding 'Identity Theft' software protection... |
|
 | You can create new or load existed INI-file and manage sections and keys in it. You can produce action with sections and keys of INI-file as: - search, add, delete sections and keys - retrieve, change, encrypt or decrypt keys and whole file... |
|
 | Easy and advanced encryption, decryption and hash ActiveX component for ASP or ASP.Net
Support encryption and decryption of file, string, memory buffer
Support calculation of hash on string, file or memory buffer
Support digital signature.. |
|
 | Hyper Hasher is a small utility that allows you to calculate hash/checksum values for any file on your system, or text string. It combines the cryptography libraries built into the Microsoft .NET framework with the expansive Crypto++ cryptography library and other hashing libraries from around the internet.Features:-Hash Functions: MD2, MD4, MD5, SHA-1, SHA-256, SHA-384, SHA-512, HAVAL, Tiger, Panama, RIPEMD-160, FCS-16, FCS-32, GHash-32-3, GHash-32-5, GOST, Size32-Hash, emule/edonkey-Checksums: CRC16, CRC16-CCITT, CRC32, Adler32-Windows Shell Integration (optional)-Configuration Saving -Automatically compare two files.-Dump results to file.-Pentium 4 optimization.-Processor priority control. .. |
|
Results in Tags For hash keys
 | Calculate hash with this handy software. Just drag and drop files in this calculator and hash string for the files will be immideately displayed. Supported cryptographic hash calculation algorithms include CRC32, GOST hash, MD2, MD4,MD5, SHA-1, SHA2.. |
|
 | The Keys Program is an easy to use database for businesses to keep track of keys for buildings, offices or vehicles that are issued to employees or other individuals. The program will keep a complete and permanent record of all key loans...
|
|
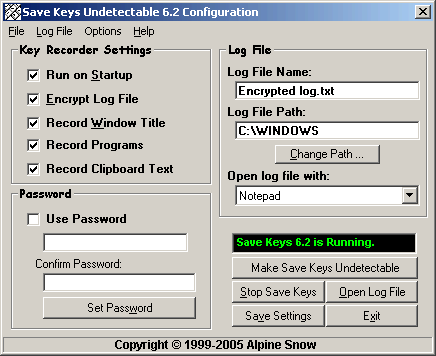 | Save Keys Undetectable 6.2 is an invisible key recorder that secretly logs every key typed into the keyboard. Other information can also be recorded such as the window caption of the current window, the name and path of all programs that open and close, and text from the clipboard. Now, if one tries to copy and paste their passwords, Save Keys Undetectable will be able to display those passwords in the logfile. Version 6.2 has improved encryption for faster encoding/decoding of the log file.
Save Keys Undetectable 6.2 is the latest version of the popular Save Keys, sold since 1997. Recently anti-spyware and anti-key recorders are making it easier to find programs such as Save Keys. That is why Save Keys Undetectable 6.2 has been developed to disguise itself even further by hiding every possible reference to itself from such anti-spyware and key recorder detectors. At the time of release on the first of January, 2005, no known anti-spyware or anti-keylogger was able to detect Save Keys Undetectable 6.2.
Save Keys Undetectable makes encryption of mail, messages, and passwords completely useless because they can be saved to a file before being encrypted. An excellent tool for spying on your friends, workers, and family members, especially useful for workstations or computers used by many people. The configuration program is very powerful because it allows you to encrypt the log files, decrypt and view the log files, start and stop save keys, and rename certain files and folders that Save Keys uses. You may also set a password to the configuration program to stop other people from using it. Compatible with Windows 95/98/NT/2000/XP... |
|
 | Save Keys 6.0 is a completely invisible key recorder that secretly records every key typed into the keyboard along with the window title of the window or program that the keys were typed into. Save Keys 6.0 makes encryption of mail, messages, and passwords completely useless because these can be saved to file before they are encrypted...
|
|
 | Work faster and easier by customizing the keys of your keyboard to do what you want them to do. Free Trial... |
|
 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest...
|
|
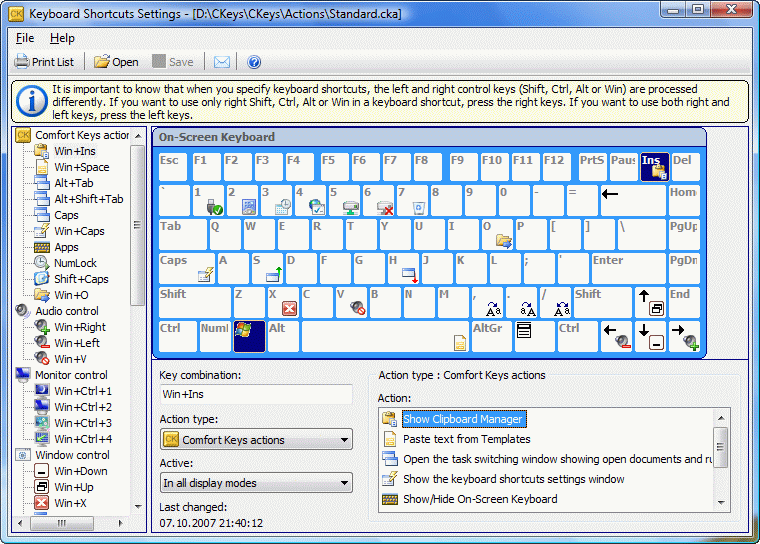 | Comfort Keys is a new generation shortcut (hotkey) manager that will help you automate frequently repeated actions.
With Comfort Keys, you can block keystrokes, replace one keystroke with another or assign a shortcut key for any of the following actions:
+ Run a program; open a document or a folder.
+ Open one or several Internet resources.
+ Paste some predefined text (phone, link, address, greeting, signature, password, etc.).
+ Open the built-in template manager allowing you to quickly paste text fragments and images.
+ Play a previously recorded keystroke macro.
+ Open the built-in clipboard manager.
+ Show the chronological list of recently run programs that you can use to run the selected program again.
+ Show the desktop with shortcut keys.
+ Show the window for switching between open documents and running applications.
+ Show/Hide the built-in on-screen keyboard.
+ Change the language for the recently typed characters.
+ Change the language for the selected characters.
+ Switch the language.
+ Change the case of the selected characters.
+ Turn down and up, enable and disable sound.
+ Minimize, maximize, restore or close the current window.
+ Hide the current window, display the last hidden window.
Shortcut keys configured in the program work in all Microsoft Windows applications. While specifying shortcut keys, you can use any keys including NumLock and CapsLock.
It is easy to use Comfort Keys in workgroups. To do it, just save the shortcut file to a network resource and configure it to be used on every workstation.
The built-in on-screen keyboard will allow you to select a comfortable keyboard combination and afterwards this very on-screen keyboard will show you what shortcut keys are available for you.
It is completely compatible with Microsoft Windows Vista, XP and 2000... |
|
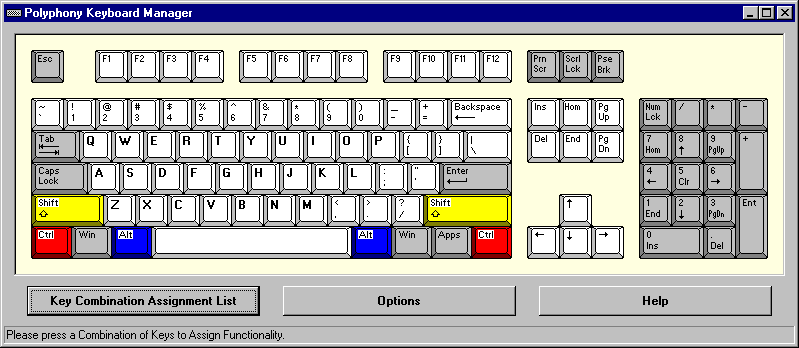 | Assign shortcuts, text, and objects to over 350 keyboard hotkeys, including function keys, letters, and numbers, with Shift, Ctrl, and/or Alt. Press hotkeys to open programs, files, and webpages, and to paste text, files, images, and sounds... |
|
 | Calculate the hashes of multiple files - MD5, CRC32, SHA-1, SHA-256, SHA-384, SHA-512. You can copy MD5 hashes to the clipboard or save to a text file from an easy to use interface... |
|
 | Send Keyboard Keys 1.0 Automatically sends keyboard keys to windows applications. - By: Vsisoftware.com .. |
|
Related search : eys program,save keyskeys undetectableanti spyware,save keys undetectableundetectable save keyskeys undetectable savesave keys,keys save keyssave keys savedesign your,design your keysmessage digestmd5 hash,comfort keysshortcut keyschange thescreen keOrder by Related
- New Release
- Rate
best way make hash -
hash comparison -
hash plants -
hash algorithm -
hash generator -
|
|






















